
Cybersecurity risk management (C-SRM) is no longer a luxury – it’s an essential tool in the digital age. As cyber threats evolve and become more prevalent, organisations of all sizes face an ever-increasing risk of data breaches, financial losses, and reputational damage. With over 4 billion data records compromised globally just last year, it’s clear that traditional security measures are no longer enough.
C-SRM offers a proactive approach to addressing these challenges. By identifying, assessing, and mitigating potential security risks before they can cause harm, C-SRM acts as a shield, protecting your organisation’s critical assets and ensuring its continued success in the digital landscape. Ignoring C-SRM leaves organisations exposed, putting them at risk of financial losses, reputational damage, and even legal consequences. By implementing a comprehensive C-SRM strategy, you can take control of your cybersecurity posture and build a more secure future for your organisation.
What is Cybersecurity Risk Management?
Cybersecurity risk management (C-SRM) is a proactive and continuous process of identifying, assessing, and mitigating the potential risks that threaten the confidentiality, integrity, and availability of an organisation’s information and systems. In simpler terms, it’s about anticipating and preventing cyberattacks before they can cause harm.
Understanding Cybersecurity Risks
Understanding the landscape of cybersecurity threats and vulnerabilities is crucial for effective cyber risk management (C-SRM). Let’s explore two key areas:
Types of Cybersecurity Threats

Organisations face diverse cyber threats, each with its own potential for harm. One common threat is malware, malicious software encompassing various tools like viruses, ransomware, and Trojans. Viruses self-replicate and spread, while ransomware encrypts data and demands a ransom for its release. Trojans disguise themselves as harmless programs, allowing attackers backdoor access to systems.
Another prevalent threat comes in the form of phishing attacks. Deceptive emails, websites, or text messages attempt to trick victims into revealing personal information, downloading malware, or clicking malicious links. These attacks often impersonate legitimate organisations or individuals. Finally, insider threats pose significant risks. These stem from individuals with authorised access, like employees, contractors, or trusted partners, who may intentionally or unintentionally cause harm. This could involve stealing data, exposing information through negligence, or sabotaging systems due to dissatisfaction.
Identification of Vulnerabilities
Understanding and addressing vulnerabilities is equally important in C-SRM. These weaknesses create entry points for attackers and can be categorised into three main areas:
- System vulnerabilities: Flaws within software, operating systems, or applications, often arising from outdated software without security patches.
- Network vulnerabilities: Weaknesses in network infrastructure, like unsecure Wi-Fi networks, misconfigured firewalls, or inadequate segmentation, making it easier for attackers to breach the network.
- Human factor: Employees are often the weakest link due to factors like lack of awareness about cybersecurity best practices, easily guessable passwords, or susceptibility to social engineering tactics used by attackers.
Addressing these vulnerabilities requires a multi-pronged approach:
- Technical measures: Patching systems regularly, implementing firewalls and anti-malware software, and utilising robust encryption technologies.
- Employee training and education: Raising awareness about cyber threats and fostering safe online behavior through training programs that emphasise secure password practices and identifying red flags.
- Policies and procedures: Establishing clear policies and incident response procedures outlining employee actions and providing a framework for handling breaches.
By understanding the evolving landscape of threats and vulnerabilities, organisations can build comprehensive C-SRM strategies, creating a more resilient and secure digital environment.
What is the Cybersecurity Risk Management Process?
Cybersecurity risk management (C-SRM) is a comprehensive process designed to identify, assess, mitigate, and recover from potential cyber threats. It involves a series of steps, typically forming a continuous cycle:
1. Identify
- Assets: This involves understanding and listing all critical assets your organisation possesses, including data, systems, hardware, software, and intellectual property.
- Threats: Identifying potential threats that could exploit your vulnerabilities, such as malware, phishing attacks, insider threats, and unauthorised access attempts.
- Vulnerabilities: Analysing your assets and systems to identify potential weaknesses, misconfigurations, or outdated software that could be exploited by attackers.
2. Assess:
- Likelihood: Determine the probability of each threat occurring based on historical data, industry trends, and current threat intelligence.
- Impact: Evaluate the potential consequences of a successful attack on each asset, considering financial losses, reputational damage, legal implications, and operational disruptions.
- Risk Level: Combine the likelihood and impact to determine the overall risk level for each identified threat and vulnerability.
3. Mitigate:
- Implement controls: Depending on the assessed risk level, implement appropriate security controls to address vulnerabilities and mitigate identified risks. This could involve access controls, firewalls, data encryption, employee training, and incident response plans.
- Prioritise mitigation: Focus on addressing the highest-risk threats first, allocating resources and efforts strategically to maximise your security posture improvement.
4. Monitor:
- Continuously monitor: Regularly monitor your systems and networks for suspicious activities, potential security incidents, and emerging threats. This could involve security information and event management (SIEM) systems, vulnerability scanners, and intrusion detection systems.
- Update assessments: As your system environment or threat landscape evolves, periodically reassess your risks and vulnerabilities to ensure your controls remain effective and your mitigation strategies are aligned with current threats.
5. Respond and Recover:
- Incident response: If a cyberattack occurs, have a well-defined incident response plan in place to quickly identify, contain, and remediate the breach. This plan should outline roles, responsibilities, communication protocols, and recovery procedures.
- Lessons learned: After an incident, analyse its root cause, identify areas for improvement in your C-SRM process, and update your strategies and controls to prevent similar incidents from happening again.
Continuous Improvement:
C-SRM is not a one-time activity. It’s an ongoing cycle where these steps are continuously revisited and refined to ensure your organisation remains prepared and resilient against evolving cyber threats. The key is to adapt and improve your C-SRM program based on new discoveries, evolving threats, and advancements in security technologies.
Frameworks and Models for Cybersecurity Risk Management
Let’s delve deeper into some of the widely recognised cybersecurity risk management frameworks and models:
NIST Cybersecurity Framework (CSF)
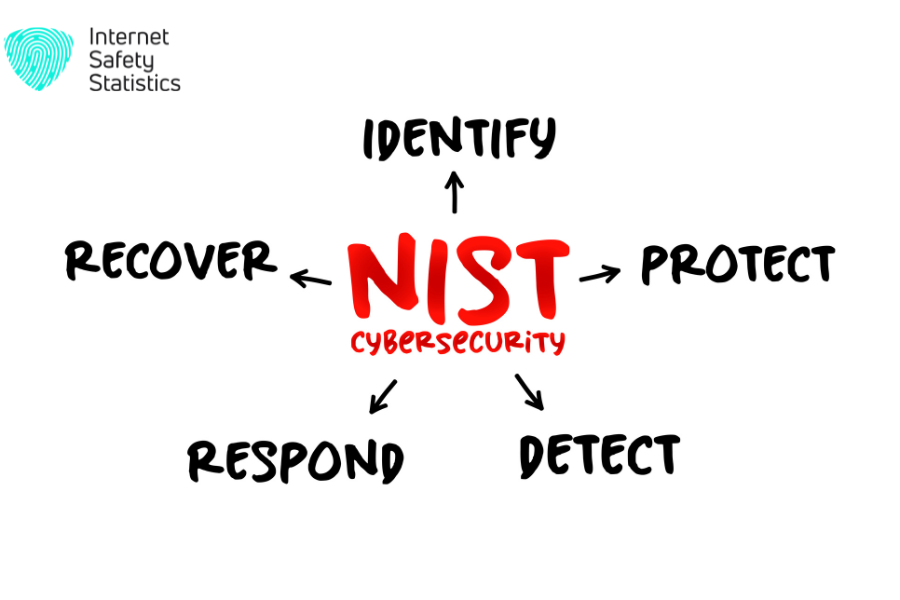
Developed by the National Institute of Standards and Technology (NIST), the CSF offers a flexible, risk-based approach to cybersecurity. It emphasises aligning cybersecurity practices with business objectives and risk tolerance. The framework is structured around five core functions:
- Identify: Understand your assets, systems, data, and the potential threats associated with them.
- Protect: Implement measures like access controls, encryption, and data backups to safeguard your assets.
- Detect: Develop robust monitoring and detection capabilities to identify potential security incidents.
- Respond: Have plans in place to respond to incidents effectively, minimise damage, and quickly resume normal operations.
- Recover: Implement processes to restore systems, data, and operations following a breach.
The NIST CSF’s adaptability makes it suitable for organisations across industries and sectors. Its focus on aligning cybersecurity with organisational goals makes it a valuable tool for strategic decision-making.
ISO 27001/27002

The International Organisation for Standardisation (ISO) 27001/27002 framework provides an internationally recognised set of standards for Information Security Management Systems (ISMS).
- ISO 27001: Specifies the requirements for establishing, implementing, maintaining, and continually improving an ISMS. It helps organisations manage information security risks across various aspects, including people, processes, and technology.
- ISO 27002: Provides comprehensive guidelines and best practices for implementing information security controls. These controls help organisations address specific risks, such as access control, data encryption, and incident response.
Achieving ISO 27001 certification demonstrates an organisation’s commitment to strong cybersecurity practices. The framework provides a structured approach for assessing and managing cybersecurity risks on a global scale.
FAIR (Factor Analysis of Information Risk)
FAIR is a quantitative model that helps organisations prioritise cybersecurity investments by calculating the potential impact of specific threats and vulnerabilities. It allows organisations to make risk-informed decisions based on financial metrics. FAIR breaks risk down into factors like:
- Loss Event Frequency: How often a specific threat might occur.
- Loss Magnitude: The potential financial impact of a security incident.
- Threat Capabilities: The ability of an attacker to exploit a vulnerability.
- Control Strength: The effectiveness of existing security controls.
The FAIR model offers a distinct advantage by translating cybersecurity risks into financial terms. This allows organisations to make more informed decisions about resource allocation and investment in cybersecurity measures. It also provides greater transparency and accountability in risk management decision-making processes.
What are the Benefits of Cybersecurity Risk Management?
Information is a valuable asset and cyber threats are constantly evolving, implementing a robust cybersecurity risk management (C-SRM) strategy is crucial for any organisation. Here are a multitude of benefits that C-SRM can bring:
Reduced Risk of Cyberattacks and Data Breaches
By proactively identifying and addressing vulnerabilities, C-SRM helps organisations patch security holes before they can be exploited by attackers. This reduces the risk of successful cyberattacks, data breaches, and the associated potential losses.
Improved Business Continuity
C-SRM focuses on ensuring the availability of critical systems and data. By implementing appropriate security controls and having a well-defined incident response plan, organisations can recover quickly from cyberattacks and minimise disruptions to normal business operations. This helps maintain productivity and minimise revenue losses.
Enhanced Compliance
Many industries have regulations and data privacy requirements that govern how organisations handle sensitive information. Implementing a C-SRM strategy demonstrates compliance with these regulations, mitigating the risk of hefty fines and legal penalties.
Boosted Stakeholder Confidence
By demonstrating a commitment to data security and taking proactive steps to safeguard information assets, C-SRM helps organisations build trust with stakeholders. This includes clients, partners, investors, and employees, fostering a sense of security and confidence in the organisation’s data security practices.
Additional Advantages
- Reduced insurance costs: Many insurance providers offer discounts for organisations with robust C-SRM programs, as they are deemed lower risk.
- Improved efficiency: C-SRM can help streamline security processes and identify areas for cost optimisation by eliminating unnecessary security investments.
- Enhanced decision-making: By having a clear understanding of cyber risks and their potential impact, organisations can make informed decisions about resource allocation and investment in security measures.
Overall, C-SRM plays a vital role in protecting an organisation’s critical assets, ensuring business continuity, and fostering trust with stakeholders. By embracing a proactive approach to cybersecurity through C-SRM, organisations can navigate the ever-changing digital landscape with increased confidence and resilience.
Challenges in Implementing Cybersecurity Risk Management
While crucial for protecting valuable assets and information in the digital age, implementing a robust cybersecurity risk management (C-SRM) strategy comes with its own set of challenges:
Resource Constraints
Implementing and maintaining a comprehensive C-SRM program often requires significant resources, including skilled personnel, advanced security tools, and ongoing training programs. Small and medium-sized businesses may find it challenging to allocate the necessary resources to build and maintain a robust C-SRM program.
Evolving Threat Landscape
The constant evolution of cyber threats creates a continuous need to adapt and update C-SRM strategies. Staying informed about the latest threats, vulnerabilities, and attack techniques requires ongoing vigilance and investment in threat intelligence resources.
User Behavior
Human error plays a significant role in successful cyberattacks. Lack of awareness about cybersecurity best practices, easily guessable passwords, and susceptibility to social engineering tactics can leave organisations vulnerable. Addressing these challenges requires ongoing user education and awareness campaigns.
Integration Complexity
Integrating C-SRM with existing IT infrastructure and business processes can be complex and time-consuming. This can be particularly challenging for organisations with complex IT environments or legacy systems.
Measuring Effectiveness
Quantifying the effectiveness of C-SRM programs can be difficult. The value of C-SRM often lies in preventing potential breaches, which are inherently difficult to quantify. This can make it challenging to obtain buy-in from leadership who may focus on short-term ROI and tangible results.
Regulatory Landscape Complexity
Navigating the ever-changing regulatory landscape can be daunting. Organisations need to stay up-to-date on evolving regulations and data privacy requirements, and ensure their C-SRM strategy aligns with these requirements to maintain compliance.
Patch Management Challenges
Keeping software and systems regularly patched is crucial for mitigating vulnerabilities. However, applying updates can be disruptive to operations and require careful planning and coordination. Balancing security needs with operational efficiency can be a challenge.
Siloed Security Efforts
Different departments within an organisation may have their own security needs and priorities. Siloed security efforts can hinder the effectiveness of C-SRM as they lack a coordinated and unified approach. Building a culture of security awareness and collaboration across departments is essential.
Despite these challenges, C-SRM remains crucial for organisations in the digital age. By acknowledging these challenges and proactively addressing them, organisations can create a more secure and resilient environment for their operations and data.
Conclusion
In today’s digital world, cyber threats are constantly evolving, demanding a proactive approach to security. Cybersecurity risk management (C-SRM) plays a critical role in safeguarding organisations’ vital assets by identifying, assessing, and mitigating potential risks before they can cause harm. By implementing a comprehensive C-SRM strategy, organisations can ensure business continuity, foster compliance and trust with stakeholders, and make informed decisions regarding security investments.
However, implementing C-SRM comes with its own set of challenges, from resource constraints to staying abreast of the ever-changing threat landscape. Additionally, navigating the complex legal and regulatory landscape with its various data privacy regulations can be daunting. These challenges highlight the importance of addressing them proactively to build a secure and resilient digital environment.
Taking a proactive approach to C-SRM is key for organisations to thrive in the digital age. By embracing C-SRM’s core principles, organisations gain a competitive edge, minimise potential damage from cyberattacks, and foster a culture of security awareness across all levels. Ultimately, C-SRM is not just a technical exercise but a strategic investment that safeguards your data, operations, and the future of your organisation.
