Cryptography, the age-old practice of secure communication, has been an essential aspect of human history. From ancient civilisations using secret codes to modern-day secure digital transactions, cryptography plays a pivotal role in safeguarding sensitive information from prying eyes. The need for strong cryptographic methods has never been more pressing as our world becomes more connected and dependent on digital technologies. We’ll delve into the realm of cryptography in this essay, looking at its core ideas, various cryptographic methods, and key uses for protecting our digital lives.
Let’s set out on a quest to discover the mysteries of cryptography and comprehend how it enables secure communication and commerce in the modern digital era.
Let us embark on a journey to unlock the secrets of cryptography and understand how it empowers us to communicate and transact securely in today’s digital age.
What is Cryptography?
Cryptography is the science and art of securing communication by converting plain, readable data into an unreadable format using mathematical algorithms. It is a crucial technique that allows users to transmit sensitive information securely over insecure networks, ensuring the confidentiality and authenticity of the data. The process involves encoding the original data (plaintext) into an encrypted form (ciphertext) using cryptographic keys.
Only authorised parties possessing the appropriate keys can decipher and access the original data. Cryptography plays a vital role in various aspects of modern life, from securing online transactions and protecting sensitive information to enabling secure communication across the internet and safeguarding digital identities.
How Cryptography works
It involves converting plaintext (readable data) into ciphertext (unreadable data) using mathematical algorithms and encryption keys. The process of encryption and decryption is the foundation of how cryptography works. Here’s a detailed explanation of how cryptography functions:
- Encryption Process:Plaintext: The original, readable data that needs to be protected is referred to as plaintext. This could be a message, a file, or any digital data.
- Encryption Algorithm: A set of mathematical operations called an encryption algorithm is applied to the plaintext. The encryption algorithm converts the plaintext into ciphertext.
- Encryption Key: A secret and unique encryption key is used by the algorithm to perform the encryption. This key determines how the plaintext is transformed into ciphertext.
- Ciphertext: The encrypted data, which appears as random characters, is known as ciphertext. It is unintelligible without the corresponding decryption key.
- Decryption Process:Ciphertext: The encrypted data, or ciphertext, is transmitted or stored securely.
- Decryption Key: To decrypt the ciphertext and revert it to its original plaintext form, a decryption key is required. The decryption key is a match to the encryption key used during the encryption process.
- Decryption Algorithm: The decryption algorithm is the mathematical process that reverses the encryption and transforms the ciphertext back into plaintext.
- Plaintext: With the correct decryption key, the decryption algorithm converts the ciphertext into its original plaintext form, allowing authorised parties to read and understand the information.
- Key Management: The security of cryptography relies heavily on the management and protection of encryption keys. The encryption and decryption keys must be kept secret from unauthorised users to ensure the confidentiality of the data.
- Different encryption algorithms and key lengths offer varying levels of security. Strong encryption algorithms with longer key lengths are more resistant to attacks and brute-force attempts to decipher the ciphertext.
Importance of Cryptography
Cryptography plays a great role in ensuring the security and trustworthiness of digital communications and data. Let’s explore its importance in detail with respect to nonrepudiation, authentication, privacy and confidentiality, and integrity:
Nonrepudiation: Nonrepudiation refers to the assurance that a recipient cannot deny receiving a message and a sender cannot deny sending it. Cryptographic techniques, especially digital signatures, provide a means to achieve nonrepudiation. By utilising their private key to sign a message, the sender can use digital signatures. The recipient can then use the sender’s public key to validate the signature.
This process guarantees the authenticity and origin of the message, making it legally binding and reducing the risk of disputes.
Authentication: It is the process of verifying the identity of users or devices to ensure that they are who they claim to be. Secure authentication methods like passwords, PINs, and digital certificates all rely on cryptography.
For instance, a user’s password is hashed using a cryptographic technique before being transferred when they log into a secure website.
The server then compares the hashed password with the stored hashed value to verify the user’s identity.
Privacy and Confidentiality: They are essential aspects of data protection. Cryptographic algorithms, particularly encryption, are used to secure sensitive information during storage and transmission. Encryption transforms data into an unreadable form using a unique key, and only authorised parties with the correct decryption key can revert it to its original form. This process ensures that even if data is intercepted by unauthorised individuals, they cannot access its contents.
Integrity: It refers to the assurance that data remains unaltered and unchanged during transmission or storage. Cryptographic hash functions are used to verify data integrity by generating a fixed-size hash value unique to the input data. Any modification to the data will result in a completely different hash value, alerting the recipient to potential tampering or corruption. This mechanism ensures that the data has not been compromised during its journey.
It is impossible to exaggerate the value of encryption in today’s digital environment. It supports the safety of sensitive information, online transactions, and communications in a variety of sectors, including finance, healthcare, government, and e-commerce. Without robust cryptographic protections, information would be open to interception, alteration, and illegal access, with serious repercussions for both people and organisations. By incorporating robust cryptographic techniques, we can safeguard data, maintain trust, and foster a secure digital ecosystem.
Types of Cryptography
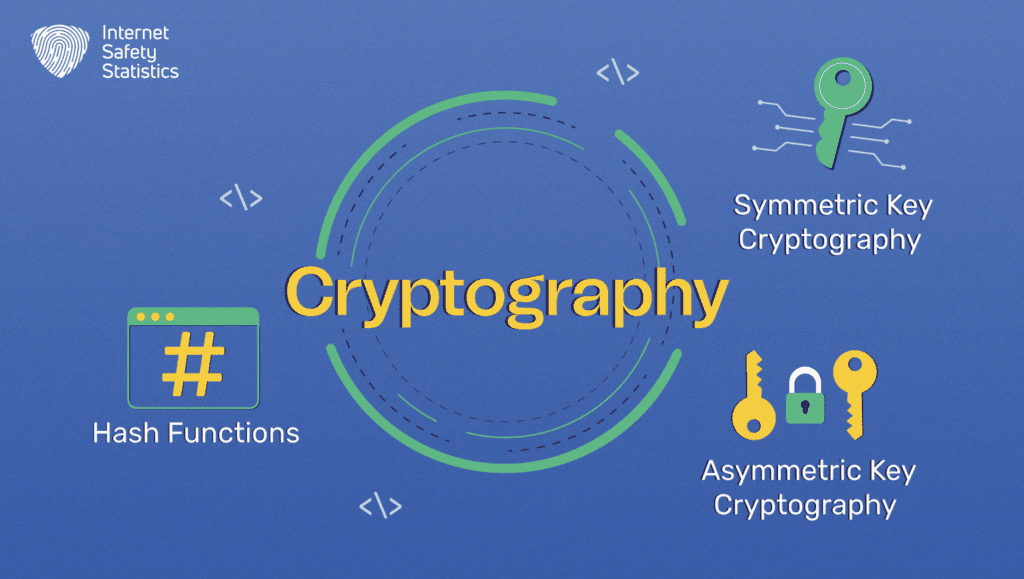
There are three main types of cryptography based on the number of keys used and their relationship:
- Symmetric Key Cryptography (Secret Key Cryptography): In symmetric key cryptography, the same secret key is used for both encryption and decryption of data. The sender and the receiver must share the secret key in advance to communicate securely. Since the same key is used for both operations, symmetric cryptography is generally faster and more efficient. However, key distribution and management can be challenging, especially in large-scale systems.
- Asymmetric Key Cryptography (Public Key Cryptography): In asymmetric key cryptography, also known as public key cryptography, two different keys are used for encryption and decryption: a public key and a private key. The public key is freely distributed and can be known to everyone, while the private key is kept secret. Data encrypted with the public key can only be decrypted with the corresponding private key and vice versa. Asymmetric cryptography provides secure key exchange and digital signatures. However, it is computationally more intensive than symmetric cryptography.
- Hash Functions (One-Way Hashing): Hash functions are a different category of cryptographic techniques. They take an input (message) and produce a fixed-size output (hash value) that is unique to that input. Hash functions are one-way, meaning it is computationally infeasible to reverse the process and obtain the original input from the hash value. Hash functions are commonly used for verifying data integrity and creating digital signatures.
Each type of cryptography has advantages and disadvantages, and they are frequently combined to offer an all-encompassing security solution.
For instance, symmetric cryptography is used for actual data encryption, while asymmetric cryptography is used for key exchange and authentication in secure communication.
Hash functions play a crucial role in data integrity verification and digital signatures.
Cryptographic Algorithms
Symmetric Key Cryptography (Secret Key Cryptography):
a. Stream Ciphers: Stream ciphers encrypt data one bit or byte at a time, making them efficient for real-time communication and high-speed data processing. They use a pseudorandom keystream, generated from the secret key, to encrypt the data stream. Common stream cipher algorithms include RC4 and ChaCha20.
b. Block Ciphers: Block ciphers divide data into fixed-size blocks and encrypt each block independently. They use the same secret key for encryption and decryption. Block ciphers can be further categorised into various modes of operation, such as Electronic CodeBook (ECB), Cipher Block Chaining (CBC), and Counter (CTR). Popular block cipher algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES).
Asymmetric Key Cryptography (Public Key Cryptography):
- RSA (Rivest-Shamir-Adleman): RSA is one of the most widely used asymmetric encryption algorithms. It relies on the difficulty of factoring large integers into their prime factors. RSA works based on the mathematical properties of two large prime numbers multiplied to produce a public key and a private key. The public key is used for encryption, while the private key is used for decryption. RSA is commonly used for securing data transmission, digital signatures, and key exchange in various applications, including online communications and secure web browsing.
- Elliptic Curve Cryptography (ECC): ECC is another asymmetric encryption technique that is gaining popularity due to its strong security and efficiency. It is based on the mathematics of elliptic curves over finite fields. ECC provides the same level of security as RSA but uses much smaller key sizes, making it more efficient in terms of computation and memory usage. This makes ECC particularly suitable for resource-constrained devices like mobile phones and Internet of Things (IoT) devices.
- Digital Signature Algorithm (DSA): DSA is a variant of the ElGamal signature scheme and is widely used for generating digital signatures. Like RSA, DSA uses asymmetric key pairs, and the private key is used for signing digital messages, while the public key is used for verifying signatures. DSA is commonly employed for ensuring the authenticity and integrity of digital documents, software updates, and communication between parties.
- Identity-based Encryption (IBE): IBE is an alternative approach to traditional public key infrastructure (PKI) where users’ identities, such as email addresses, can directly serve as public keys. This means that anyone can encrypt a message using the recipient’s identity, and only the intended recipient, with the corresponding private key, can decrypt the message. IBE simplifies the key management process, making it easier to deploy secure communication in large-scale systems.
- Public Key Cryptography Standards (PKCS): PKCS is a set of standards developed by RSA Security that defines various cryptographic protocols and formats. These standards cover topics such as RSA key generation, digital signatures, encryption, and certificate management. PKCS standards play a crucial role in ensuring interoperability and compatibility between different cryptographic systems and applications.
- Diffie-Hellman and Key Exchange Algorithm (KEA): The Diffie-Hellman algorithm, along with its variants, is a key exchange algorithm used to securely establish shared secret keys between two parties over an insecure channel. This shared key can then be used for symmetric encryption. The KEA algorithm is based on the Diffie-Hellman concept and is used for exchanging encryption keys in secure communications.
Each of these cryptographic methods is essential for securing digital communications and shielding private data from intrusion and alteration. Understanding their strengths and applications is essential for building secure and robust systems in today’s interconnected world.
Hash Functions (One-Way Hashing): Hash functions are a different category of cryptographic techniques. They take an input (message) and produce a fixed-size output (hash value) that is unique to that input. Hash functions are one-way, meaning it is computationally infeasible to reverse the process and obtain the original input from the hash value. Hash functions are commonly used for verifying data integrity and creating digital signatures.
Each type of cryptography has advantages and disadvantages, and they are frequently combined to offer an all-encompassing security solution.
For instance, symmetric cryptography is used for actual data encryption, while asymmetric cryptography is used for key exchange and authentication in secure communication.
Hash functions play a crucial role in data integrity verification and digital signatures.
Applications of Cryptography
Cryptography finds widespread applications in various domains to ensure the security and privacy of digital information. Let’s explore these applications in detail:
Cryptocurrencies: To enable secure and decentralised transactions, cryptocurrencies like Bitcoin, Ethereum, and others significantly rely on cryptography techniques. Every transaction is verified and secured using cryptographic hashing and digital signatures using blockchain technology, a sort of distributed ledger system. These cryptographic algorithms ensure the integrity and immutability of transaction records, making cryptocurrencies resistant to fraud and unauthorised access.

Authentication: Cryptography plays a crucial role in user authentication mechanisms. When a user logs into a system or website, their credentials (like passwords) are encrypted using cryptographic hash functions before being stored in databases. During subsequent login attempts, the system hashes the entered credentials and compares them with the stored values to verify the user’s identity. This process prevents the exposure of plain-text passwords, reducing the risk of unauthorised access.
Electronic Signatures: Electronic signatures are digital equivalents of handwritten signatures used to authenticate the authenticity of digital documents. Cryptography enables the generation of digital signatures using asymmetric key pairs. The signer’s private key is used to sign the document, and the recipient can use the signer’s public key to verify the signature and ensure the integrity of the document.
Digital Currencies: Beyond cryptocurrencies, cryptography is also applied in various digital payment systems and mobile payment apps. Secure communication protocols and encryption techniques ensure the confidentiality and integrity of financial transactions, protecting sensitive financial information from unauthorised interception.
Secure Web Browsing: Secure web browsing relies on cryptographic protocols such as SSL/TLS to establish encrypted connections between web browsers and servers. This encryption ensures that data exchanged during online transactions, such as credit card information, login credentials, and personal details, remains confidential and protected from eavesdropping.
End-to-End Encryption: End-to-End Encryption (E2EE) is used in messaging and communication platforms to secure messages and data from being intercepted by unauthorised parties. E2EE ensures that only the sender and the intended recipient can access the content, as all communication is encrypted and decrypted at the endpoints.
Computer Passwords: Cryptography is instrumental in protecting user passwords stored on computers and online platforms. Instead of storing plain-text passwords, systems use cryptographic hashing to convert passwords into irreversible hash values. This approach ensures that even if the password database is compromised, attackers cannot retrieve the original passwords.
Cryptography’s versatile applications extend beyond these examples, finding utility in secure cloud storage, virtual private networks (VPNs), secure email communication, digital rights management, and more.
