Most people confuse ethical hacking and cybersecurity. Although they are interrelated terms, they differ significantly. Cybersecurity is a broad domain that includes diverse computer security mechanisms, whereas ethical hacking is one of the cybersecurity mechanisms. In the following lines, let’s discuss both terms in detail and explore their differences.
Types of Hackers
Before we know what cybersecurity and ethical hacking mean, let’s find out what hacking is. With the aim of stealing sensitive data or gaining money, hacking is the exploitation of networks or digital devices’ weaknesses (i.e. bugs) to gain unauthorised access. The persons who do these malicious practices are called hackers. However, not all hacking is malicious, and not all hackers are unethical. There are different types of hackers named according to their intention of hacking. The first three types are the main ones.
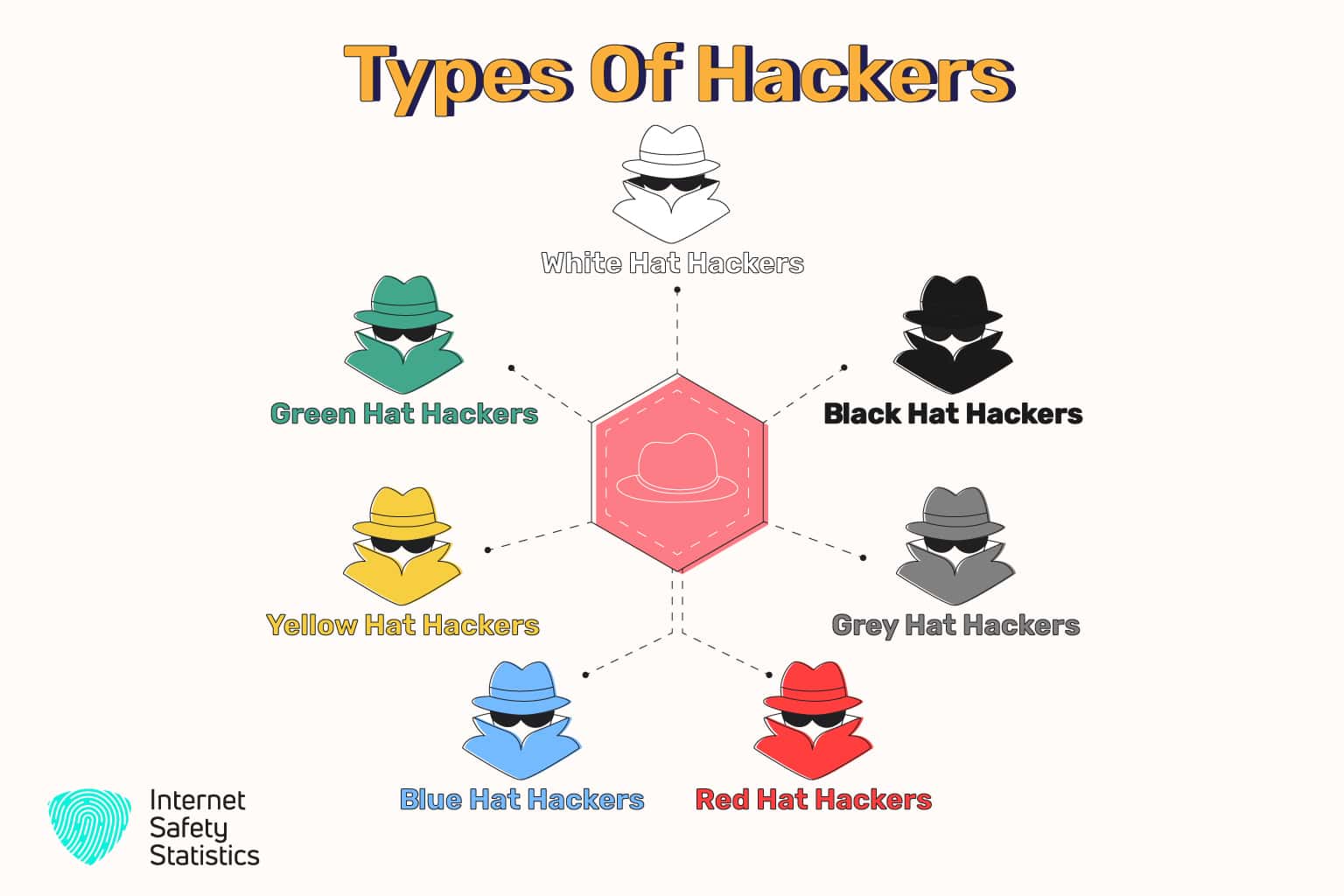
1. Black Hat Hackers
A black hat hacker is an unethical hacker who uses illegal techniques to violate the security of a computer or network and destroy information. They gain unauthorised access to a computer or a system and exploit security vulnerabilities for personal or financial gain. For example, they may send phishing emails to steal identities or sell sensitive information.
2. White Hat Hackers
On the contrary, a white hat hacker practices ethical hacking. That is why s/he is also known as an ethical hacker. They aim to perform a penetration test, an authorised simulated cyberattack against a computer system. They perform pen tests to discover system vulnerabilities and evaluate systems’ security. Then, they report security vulnerabilities to developers to fix them. They also build antivirus, firewalls, and other security software. We will focus on this type of hacker in this article.
3. Grey Hat Hackers
A grey hat hacker is somewhere between white and black hat hackers. They sometimes violate typical ethical standards without malicious intent or personal benefit. They compromise an organisation’s network to disclose the vulnerabilities or threats to this affected place. Occasionally, organisations pay them to provide solutions or tools to fix vulnerabilities and bugs.
4. Red Hat Hackers
Similar to a grey hat hacker, a red hat hacker chooses the wrong path to do the right thing. Trying to save the world from evil hacking, they deploy cyberattacks against black hat hackers. So, they infect the systems of the black hat hackers with malware and destroy their servers.
5. Blue Hat Hackers
A blue hat hacker is a security expert working outside the organisation that invites them to find security vulnerabilities and bugs in its new software or system. Some blue hat hackers are known as blue hat Microsoft hackers because Microsoft organises periodic conferences for those hackers to test its Windows programmes.
6. Yellow Hat Hackers
A yellow hat hacker focuses on hacking or stealing social media network accounts. Their motivation is to take revenge on a person or organisation or gain access to personal information.
7. Green Hat Hackers
There is also a green hat hacker who is a hacker in training. S/he is a hacking newbie who lacks the technical hacking skills of an experienced hacker. S/he might unintentionally cause harm to others while practising due to their lack of experience and skills.

Who is the Most Popular Hacker in the World?
Kevin Mitnick is the world’s best and most renowned hacker. He started his career in hacking at an early age; however, he was arrested for being a black hat hacker. After release, he established his cybersecurity consulting firm, thus linking white and black hat hackers.
What is Cybersecurity?
First, let’s talk about the broader term that includes ethical hacking: cybersecurity. Cybersecurity is the process or practice that defends computers, networks, and sensitive data against unauthorised access or malicious attacks. It requires specific tools to provide its users with the best security environment. As the number of cybercrime grows, it is becoming more and more critical.
Individuals need cybersecurity systems and programmes to prevent unauthorised access and protect their devices, data stored online, and accounts. For example, antivirus software can detect malicious activity and warn the user immediately. Additionally, if the user forgets their password, the website validates their identity securely by receiving a text or voice code on their phone. Then, the website allows them to reset their password.
On the other hand, enterprises and governmental organisations have IT teams that may include a Network Security Engineer, a Systems Security Administrator, a Security Architect, and a Penetration Tester. They also need proper cybersecurity systems to protect the enormous amounts of sensitive data they store online. What supports their cybersecurity process is the risk register file which lists all risks and their solutions. Each organisation manages their risk register file, preventing any security breach.
What is Ethical Hacking?
After establishing all security controls, it is time to test and validate the security system against all possible security breaches. This process is known as ethical hacking. An ethical hacker uses the same tools and techniques the hacker uses but with good intent. They aim to ensure the system is fully secured and nobody can bypass the cybersecurity system.
During this process, the ethical hacker examines the system to check whether security controls protect the website/application. They try to discover all weaknesses and vulnerabilities in the system and fix them before an unethical hacker exploits them.

Difference Between Ethical Hacking and Cybersecurity
Securing the system and the data is the objective of ethical hacking and cybersecurity. However, the approach towards this objective differs considerably. Let’s explore the key differences between ethical hacking and cybersecurity.
| Cybersecurity | Ethical Hacking |
|---|---|
| Cybersecurity involves identifying and resolving security issues to protect the data and the system from malicious activities. It includes various network and information security techniques, like digital forensics, data security, and ethical hacking. | Ethical hacking involves finding vulnerabilities in the system and reporting them to the company’s owner. It is part of cybersecurity. So, all ethical hackers are cybersecurity experts, but not all cybersecurity experts are ethical hackers. |
| Main Aim of Cybersecurity | Main Aim of Ethical Hacking |
| Cybersecurity uses defencive security measures. It focuses on how to defend the system. It is also responsible for developing access privileges, the rights and abilities assigned to an authorised user. | Ethical hacking uses offencive security measures. It focuses on how to attack the system legally while adhering to all ethical guidelines, like obtaining consent or permission from the owner. It is also responsible for providing reports on how the hacking was performed. |
| Process of Cybersecurity | Process of Ethical Hacking |
| Cybersecurity experts do regular maintenance to make sure the security system is updated. | Ethical hackers regularly test the system to find out the bugs and weaknesses. |
| Phases of Cybersecurity | Phases of Ethical Hacking |
| The cybersecurity framework of the NIST (National Institute of Standards and Technology) is based on five primary phases. These five pillars form the basis of all successful cybersecurity programmes. They are: 1. Identify: In this stage, the cybersecurity expert does the following: -Identifying devices, facilities, and software assets, -Understanding the system, -Identifying cybersecurity policies and making sure they comply with the company’s regulatory requirements, -Identifying security threats, vulnerabilities, and risk-response activities, and -Setting up a monitoring process that tracks user access and behaviour. 2. Protect: The Protect stage outlines the processes the company must have to ensure it can limit the harmful impact of a breach. It encompasses several activities, which are: -Limiting access to compromised assets, -Providing staff with cybersecurity training according to their roles and system privileges, -Managing the company’s data according to a defined risk strategy, -Protecting the company’s data and systems by implementing security procedures, -Performing necessary repairs and maintenance, and -Implementing protective technology solutions. 3. Detect: The prompt detection of breaches is vital to network security. So, the cybersecurity expert must assume that a breach is inevitable. This way, s/he can discover breaches and cybersecurity events promptly. Here are some actions related to this stage: -Implementing continuous network and user activity monitoring, -Verifying the effectiveness of the network protective measures, and -Evaluating your awareness of unusual behaviours and events. 4. Respond: After detecting a breach, the cybersecurity expert must take appropriate actions quickly, depending on the breach’s severity and type. Rapid response minimises the damage that critical functions may be exposed to. Here are some activities that help prevent the spread of a breach: -Mitigating actions, and -Improving and learning consistently to avoid similar future breaches. 5. Recover: Following a breach, the Recover stage aims to return to normal operations and performance and restore lost data. It has several actions, including: -Setting up recovery planning procedures in advance, -Determining the areas that require improvements, -Implementing new solutions based on previous cybersecurity incidents, -Coordinating communications with internal and external stakeholders after an incident, and -Ensuring the staff understand what they can do to help recover the full functionality of the business. | Ethical hacking is also based on five steps. It begins with looking for ways to hack into the system, followed by exploiting vulnerabilities, gaining access, and maintaining steady access, and ends with covering tracks. Here are the five phases: 1. Reconnaissance: Reconnaissance is also known as the information-gathering or the preparatory phases. Its goal is to collect a lot of information about the target networks, devices, and systems before launching an attack. This data is likely to be passwords, network topology, and names of important employees and their positions. There are two types of reconnaissance: -In passive reconnaissance, the ethical hacker attempts to gather information without engaging with the target’s systems. It relies on public data available on social media and websites, like IP addresses, email addresses, hostnames, and domain names. –Active reconnaissance involves the ethical hacker interacting directly with the target’s systems. They use tools to send different types of requests to the target computer and obtain information, like open/closed ports, banner grabbing, services that are running, and the Operating System of a machine. 2. Scanning: Then, the ethical hacker applies all the information obtained during the previous stage. It aims to find detailed information and vulnerabilities in the target network. Scanning could be basically of three types: –Port Scanning uses dialers, port scanners, or other data-gathering tools to detect open exploited vulnerabilities running services on the target host. It could be divided into five types: Ping Scan, TCP Half Open, TCP Connect, UDP, and Stealth Scanning. –Network Scanning detects active devices on the target network and discovers IP addresses and operating systems. The ethical hacker uses this type to identify vulnerabilities and strengthen the company’s network. –Vulnerability Scanning uses OpenVAS, Netsparker, and other automated tools to detect vulnerabilities in the target network, system, or device. 3. Gaining Access Now, it is time for the ethical hacker to do the actual hacking. The popular technique used to gain unauthorised access is social engineering. Using the information obtained and analysed from the previous stages, they exploit all the exposed vulnerabilities to gain unauthorised access and control the connected systems. Now, they can steal sensitive data or download malicious code or software onto the target’s computers, networks, systems, or applications. 4. Maintaining Access Once ethical hacker accesses the target system, they make sure they have persistent access to the server or resources until they complete their malicious activities. They use trojans and backdoors to get in and out of the system anonymously, even if the target has detected and closed this open port. 5. Clearing Tracks The last step to complete the ethical hacking process is to remain anonymous. In this phase, the ethical hacker makes sure they leave the system with no evidence or clue that could be traced. It includes many measures, such as: -Clearing cache and cookies to erase the digital footprint, -Deleting or corrupting all the log files, -Modifying logs or registry values, -Closing all open ports, -Using a Virtual Private Network (VPN), and -Deleting/uninstalling all the folders, applications, and software created/ downloaded by the ethical hacker. |
| Types of Cybersecurity | Types of Ethical Hacking |
| Cybersecurity can be categorised into different types that include: –Network Security -Data Security -Systems Security –Cloud Security -Application Security -Mobile Security -Endpoint Security -Internet of Things (IoT) Security -Infrastructure Security -Security Architecture -Identity Management | Hackers can hack a system, website, device, process, network and more. There are several types of ethical hacking, such as: -System hacking -Web server hacking -Web application hacking -Hacking wireless networks -Black-box testing -White-box testing -Grey-box testing -Social engineering |
| Roles of Cybersecurity | Roles of Ethical Hacking |
| Cybersecurity offers various roles, such as: -Security Analyst -SOC Engineer -Cyber Forensics Expert -Chief Information Security Officer (CISO) | Ethical hacking involves many professions, like: -Penetration tester -Security Manager |
| Skills Required for Cybersecurity Jobs | Skills Required to Become an Ethical Hacker |
| To work in the cybersecurity field, cybersecurity experts should have professional skills, including: -Problem-solving -Curiosity to learn -Attention-to-detail -Communication -Scripting –Operating systems -Digital forensics -Technical aptitude They should also be knowledgeable about all the following: -Hacking techniques -Cybersecurity across various platforms -Alert fatigue -Kill chains -Zero-day attacks -Risk analysis -Threat intelligence analysis -Networking and system administration -Security auditing -Application security development -Security incident handling and response | To work in ethical hacking and perform it efficiently, an ethical hacker should have some professional skills, like: -Communication -Computing –Programming -Networking -Scripting -Coding -Troubleshooting -Curiosity to learn -Attention-to-detail -Problem-solving They should also have knowledge of: -All security measures -Programme codes -Systems -Networks -Databases -Database management systems, like MySQL and Oracle. -Operating systems -Hacking tools –Search engines -Servers -Applications -Social engineering –Cloud computing -Wireless network hacking |

Importance of Ethical Hacking in Cybersecurity
The importance of ethical hacking in cybersecurity is crucial. It manages, controls, and prevents cyberattacks, and makes businesses and organisations avoid security breaches, thus keeping them away from destructive consequences. By doing real-world testing, ethical hackers use the perspectives and techniques of black hat hackers to find potential vulnerabilities. Then, they try to fix these weaknesses before the bad hackers exploit them.
What is The Future of Ethical Hacking in Cybersecurity?
Ethical hacking has a bright future. As long as cyberattacks and security breaches increase, the demand for ethical hackers is rising. Artificial intelligence hacking is also a potential future danger, and systems will require more ethical hackers.
How Could You Be A Certified Ethical Hacker?
Developing your ethical hacking skills takes between 18 months to six years. The fewer relevant skills you have, the longer time you will take. The Certified Ethical Hacker (CEH) certification helps you perform penetration testing, detect vulnerabilities, and prevent cyberattacks. You can choose the right course according to your preferences and interests.
In Summary,
Ethical hacking and cybersecurity aim to protect the systems and the data; however, they use different methods to approach it. We dug deep into ethical hacking and cybersecurity and explored the differences between them. Cybersecurity is the overall strategy of protecting against cyberattacks, while ethical hacking is a specific technique used within that strategy to proactively identify and address vulnerabilities.
