Proxy servers, often operating quietly behind the scenes, are the unsung heroes of the digital world. They play a vital role in internet security, content delivery, and privacy protection, and yet many users remain unfamiliar with their functionality and significance. In this article, we will demystify proxy servers, shedding light on how they work, why they matter, and the diverse ways in which they can be harnessed to enhance your online experience.
In an era where cybersecurity threats loom large and privacy concerns continue to grow, understanding the role of proxy servers is crucial. Whether you’re a business looking to safeguard sensitive data, a privacy-conscious individual, or a developer striving to optimise network performance, proxy servers offer a multifaceted solution that warrants exploration. Join us on this journey through the inner workings of proxy servers, their various applications, and how they impact your online encounters.
What is a Proxy Server?
A proxy server is an intermediary or go-between that stands between your device and the internet. It acts as a representative on your behalf, intercepting your requests to access websites, services, or online resources. It forwards these requests to the target server and, in turn, manages the responses, providing a range of functions, such as request modification, caching, security measures, and privacy protection. Proxy servers enhance security, performance, and control in your online activities, making them versatile tools for various internet-related purposes.

How do Proxy Servers work?
To demystify the world of proxy servers, let’s start by unravelling their basic functioning and how they operate as intermediaries in the realm of Internet communications.
1. Basic Functioning
At its core, a proxy server acts as an intermediary between your device and the internet. It functions somewhat like a middleman, handling the requests and responses between your computer or device and the websites or services you wish to access.
• Request Handling: When you initiate a request to access a website, for instance, your request is not sent directly to the website’s server. Instead, it is intercepted by the proxy server. This request could be for a web page, a file, or any online resource.
• Forwarding the Request: it then takes your request and forwards it to the target server, which could be a website, an application, or any online service. It essentially acts as your representative in the digital realm.
• Response Handling: Once the target server processes your request and generates a response (which could be a web page, a file, or any data), the proxy server intercepts this response before it reaches your device. It examines the response, potentially making modifications, and then forwards it to your device.
2. Interception and Forwarding
One of the key roles of a proxy server is to intercept data passing between your device and the internet. It does this by sitting in the data path, acting as a gatekeeper, and scrutinising the information flowing back and forth.
• Request Modification: Proxy servers can modify requests before forwarding them. For example, they can add additional headers or change the user-agent string to mimic a different device or browser.
• Caching: Some proxy servers store copies of frequently requested resources locally. If another user makes a similar request, the proxy server can provide the cached version, reducing the load on the target server and improving response times.
• Filtering and Security: Proxy servers are often employed to implement security measures and content filtering. They can block access to specific websites or content categories, protecting users from malicious or inappropriate content.
• Anonymity: Proxy servers can be configured to obscure your IP address and location. This anonymity is particularly useful for users who wish to maintain their privacy while browsing the web.
In essence, a proxy server is a versatile tool that can enhance security, improve performance, and provide various levels of anonymity and control in your online activities. Its role as an intermediary in Internet communications empowers you to tailor your online experience according to your specific needs and preferences.
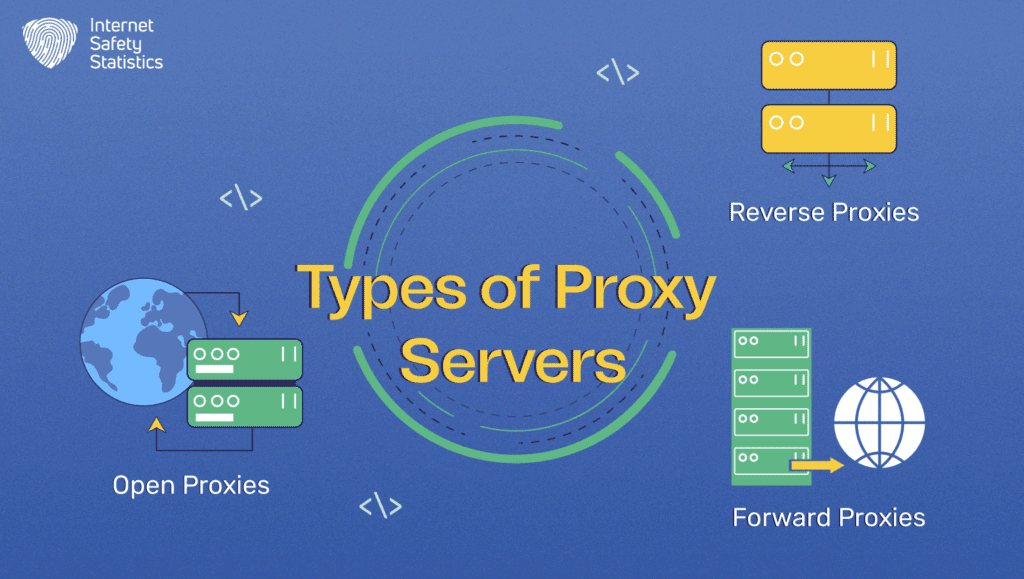
Types of Proxy Servers
Proxy servers come in various flavours, each tailored for specific use cases and functionalities. Let’s explore the main types:
1. Forward Proxies
Let’s dive deep into the functionality of forward proxies and their use cases.
Functionality
A forward proxy, often simply referred to as a “proxy”, acts on behalf of client devices seeking access to the internet. It intercepts requests from these clients and forwards them to the target servers. In other words, it represents the client to the internet.
Use Cases
• Privacy and Anonymity: Forward proxies can hide a user’s IP address, enhancing online privacy.
• Content Filtering: Organisations often use forward proxies to block access to specific websites or content categories.
• Caching: Caching proxies store frequently accessed content locally, reducing the load on target servers and improving response times.
2. Reverse Proxies
The second type is reverse proxies. Let’s explore their functionality and use cases.
Functionality
A reverse proxy, also known as an “inbound proxy”, stands between client devices and backend servers. It intercepts requests from clients and forwards them to the appropriate backend server. In this case, it represents the internet to the backend server.
Use Cases
• Load Balancing: Reverse proxies distribute incoming traffic across multiple backend servers to optimise performance and maintain availability.
• SSL Termination: They handle SSL encryption/ decryption, freeing up backend servers from this resource-intensive task.
• Security: Reverse proxies can serve as a security barrier, protecting backend servers from direct exposure to the internet.
3. Open Proxies
Another type is the open proxies. Let’s learn more about their functionality and use cases.
Functionality
Open proxies are publicly accessible proxy servers that anyone can use without authentication. They are typically offered for free or as paid services.
Use Cases
• Bypassing Censorship: In regions with restricted internet access, open proxies can help users access blocked content.
• Anonymity: Open proxies can provide some level of online anonymity, though they often come with security risks.
• Testing and Debugging: Developers and testers can use open proxies to examine how web applications behave in different locations.
These different types of proxy servers cater to various needs, from enhancing online privacy and security to optimising network performance and circumventing internet censorship. The choice of proxy server depends on your specific requirements and the functionalities you seek in your online interactions.
Proxy Server Setup and Configuration
Configuring a proxy server may seem like a complex task, but with the right guidance, it can be a straightforward process. Here’s a step-by-step guide in more human-friendly terms, complete with software recommendations and best practices:
1. Choose Your Proxy Software: Start by selecting proxy server software that aligns with your goals. Popular options include Squid, Apache, and Nginx for forward proxies and Nginx or HAProxy for reverse proxies.
2. Install the Chosen Software: Download and install the selected software on a server or computer that will act as your proxy. Follow the installation instructions provided by the software.
3. Configure Basic Settings: Define your proxy server’s basic settings, including the listening port and the protocol (HTTP, HTTPS, or SOCKS) you want to use. These settings are typically found in the software’s configuration files.
4. Set Up User Authentication: If you want to restrict access to your proxy server, consider setting up user authentication. This ensures that only authorised users can connect.
5. Define Access Controls: Configure access controls to specify which clients or IP addresses can connect to your proxy server. This is crucial for security and access control.
6. Enable Logging: Turn on logging to keep a record of connections and activities. This can be invaluable for troubleshooting and monitoring.
7. Implement Content Filtering (Optional): If content filtering is part of your proxy server’s purpose, set up filters and rules to control the types of websites or content users can access.
8. Test Your Configuration: Before deploying your proxy server, thoroughly test your setup to ensure it’s working as intended. Verify that it can intercept and forward requests successfully.
9. Monitor Performance: After deployment, regularly monitor your proxy server’s performance and logs. Make adjustments as needed to maintain optimal functionality.
10. Keep Software Updated: Stay current with software updates and security patches to protect your proxy server from vulnerabilities.
Setting up and configuring a proxy server requires some technical know-how, but with the right software and a methodical approach, it can be a manageable process. Proper configuration ensures that your proxy server effectively serves its purpose while providing the security and control you need for your online activities.
Benefits and Advantages of Using Proxy Servers
Proxy servers offer a range of real-world advantages that make them valuable tools for individuals, businesses, and organisations.
1. Enhanced Security
Proxy servers act as gatekeepers, screening incoming and outgoing web traffic. They can provide an added layer of security by filtering out malicious content, potentially harmful websites, and known threats. This helps protect your device and network from online dangers, making your digital experience safer. In a corporate setting, a proxy server can prevent employees from accessing websites with known malware or phishing links, reducing the risk of data breaches.
2. Improved Anonymity
Using a proxy server can make your online activities more anonymous. By masking your IP address and location, you can maintain a degree of privacy when browsing the internet. This can be especially useful for users who want to keep their online identity hidden. Journalists in repressive regimes may use them to conceal their online activities while researching sensitive topics.
3. Network Performance Optimisation
Proxy servers, particularly caching proxies, store frequently accessed content locally. This means that when multiple users request the same content, the proxy can provide it quickly from its cache, reducing the load on the original servers. This can significantly boost the speed and efficiency of your internet connection. Content delivery networks (CDNs) use proxy servers to distribute content closer to users, reducing latency and ensuring faster loading times for websites and streaming services.
4. Content Filtering
Proxy servers can be configured to block access to specific websites or content categories. This feature is handy for organisations that want to regulate or restrict internet access for security or productivity reasons. Educational institutions use these proxies to prevent students from accessing inappropriate or distracting websites during school hours.
5. Bypassing Censorship
In regions with strict internet censorship, proxy servers, particularly open proxies, can help users access blocked content and express themselves freely online. Citizens in countries with heavy internet restrictions may use them to connect to the free and open web.
Proxy servers are versatile tools that provide tangible benefits, whether you’re looking for a safer online experience, enhanced privacy, faster internet speeds, or control over content access. Understanding their advantages can help you make the most of your internet interactions.

Proxy Servers’ Limitations and How to Address Them
While proxy servers offer numerous advantages, they do come with their share of limitations and potential drawbacks. Here’s an exploration of these limitations, along with strategies to mitigate them:
1. Performance Concerns
• Limitation: Proxy servers can introduce latency into your internet connection, particularly if they are distant from your location or if there’s a heavy load on the server. This can slow down your online activities.
• Mitigation: Opt for proxy servers that are geographically closer to you or use CDNs to distribute content efficiently. Also, keep an eye on your proxy server’s performance and consider load balancing if necessary.
2. Security Vulnerabilities
• Limitation: A misconfigured or poorly maintained proxy server can become a security vulnerability. Attackers may exploit vulnerabilities in proxy software or use the proxy server to hide their malicious activities.
• Mitigation: Regularly update your proxy server software to patch known vulnerabilities. Also, implement strong security practices, including access controls, user authentication, and monitoring for suspicious activities. Regularly review and audit your server’s configuration.
3. Single Point of Failure
• Limitation: If your proxy server goes down, it can disrupt internet access for connected clients. This makes it a single point of failure in your network.
• Mitigation: Employ redundancy and fail-over mechanisms to ensure uninterrupted service. Distribute your proxy servers across multiple locations and implement load balancing to automatically route traffic to operational servers.
4. Limited Content Access
• Limitation: Some websites or services may block access to known proxy server IP addresses, preventing you from accessing their content.
• Mitigation: Use rotating or residential proxy services that change IP addresses regularly, making it harder for websites to block your access.
5. Privacy Concerns
• Limitation: While proxy servers can provide anonymity, they can also be configured to log user activities. This may raise privacy concerns.
• Mitigation: Choose proxy servers with a clear privacy policy or set up your own server with strict logging policies. Review the proxy server’s logging settings and tailor them to your privacy needs.
Notable Proxy Server Software and Tools
Proxy server software and tools play a pivotal role in enabling various functionalities, from enhancing security to optimising network performance. Here’s an overview of some popular options, along with their key features and typical use cases:
1. Squid
• Key Features: Squid is a widely used, open-source caching proxy server known for its robust performance and extensive configuration options. It supports HTTP, HTTPS, FTP, and more.
• Use Cases: Squid is frequently used as a forward proxy for content caching and as a reverse proxy for load balancing and content delivery. It’s popular in CDNs and web accelerators.
2. Nginx
• Key Features: While Nginx is primarily known as a high-performance web server, it’s also an efficient reverse proxy. It offers features like load balancing, SSL termination, and web acceleration.
• Use Cases: Nginx is often used as a reverse proxy in front of web servers to improve web application performance and security. It’s a favourite for load balancing and handling SSL encryption.
3. Apache HTTP Server
• Key Features: Apache is a well-established, open-source web server, and it can function as a reverse proxy using modules like mod_proxy and mod_proxy_http.
• Use Cases: Apache is suitable for organisations familiar with its web server capabilities. It’s commonly used as a reverse proxy to forward client requests to backend servers.
4. HAProxy
• Key Features: HAProxy is a high-performance TCP/HTTP load balancer and proxy server known for its speed and scalability. It excels in load balancing and SSL offloading.
• Cases: HAProxy is ideal for balancing traffic across multiple servers to improve performance and reliability. It’s often used in environments with high traffic loads.
5. Privoxy
• Key Features: Privoxy is an open-source, non-caching web proxy with filtering capabilities. It can remove ads, cookies, and other web annoyances.
• Use Cases: Privoxy is employed for ad-blocking and enhancing online privacy. It can be configured as a local proxy for web browsers.
6. Shadowsocks
• Key Features: Shadowsocks is a lightweight, secure, and open-source proxy server designed for circumventing internet censorship. It uses encryption for secure data transfer.
• Use Cases: Shadowsocks is popular in regions with strict internet censorship, as it helps users access restricted content and maintain online privacy.
7. Tor (The Onion Router)
• Key Features: Short for The Onion Router, Tor is a privacy-focused network that offers anonymous browsing. It routes user traffic through a network of volunteer-operated servers to anonymise data.
• Use Cases: Tor is used by individuals seeking maximum online anonymity and privacy, such as activists and journalists in high-risk regions.
8. Charles Proxy
• Key Features: Charles is a web debugging proxy that allows users to inspect HTTP and SSL/HTTPS traffic between their devices and the internet. It’s commonly used for debugging and testing purposes.
• Use Cases: Developers and testers use Charles Proxy to analyse and debug web traffic to identify issues or improve web applications.
These proxy server software and tools cater to a wide range of use cases, from improving web performance and security to maintaining online privacy and circumventing censorship. The choice of software depends on specific needs and expertise, so selecting the right one is essential for achieving the desired results.
In Conclusion
Proxy servers are not just digital sentinels; they’re versatile tools enabling safer, more controlled, and more efficient internet experiences. By comprehending their strengths and weaknesses, users can optimise their usage, effectively fortifying their online presence in an ever-evolving digital landscape.
