
Every bit of internet data, from personal conversations to sensitive transactions, is susceptible to prying eyes. Understanding how to strengthen your online presence is paramount in this digital age. So, encrypting your internet connection is essential, as the security of our online activities has never been more critical.
This article aims to be your guiding light in digital security, focusing on the indispensable skill of encrypting your internet connection. Join us as we delve into the intricacies of connection encryption, unravelling the tools and techniques to transform your online experience into a fortress of privacy and security.
What Is Connection Encryption?
Connection encryption refers to securing data during transmission between two points over a network, such as the Internet. Its key aspects include:
1. Secure Communication: Connection encryption ensures that data exchanged between devices, servers, or users is protected from eavesdropping and interception by encrypting the data as it travels over the network.
2. Encryption Protocols: Various encryption protocols are used to implement connection encryption. Examples include SSL (Secure Sockets Layer), TLS (Transport Layer Security), and IPsec (Internet Protocol Security). These protocols use cryptographic techniques to secure the data in transit.
3. Encryption Algorithms: The encryption process uses mathematical algorithms to scramble the data into an unreadable format (ciphertext). The algorithms rely on encryption keys, and the connection’s security depends on these keys’ strength and complexity.
How Do You Master Encrypting the Internet Connection for Free?
A virtual private network (VPN) is a free way to encrypt the internet connection. Free VPN services like ProtonVPN, Windscribe, or TunnelBear are available. Remember that free VPNs might have limitations, such as data caps or slower speeds.
Additionally, many websites now use HTTPS to encrypt data in transit. You can install browser extensions like HTTPS Everywhere to secure your connection on supported websites. Remember, while these methods can enhance online security, no solution is foolproof, so always stay vigilant.
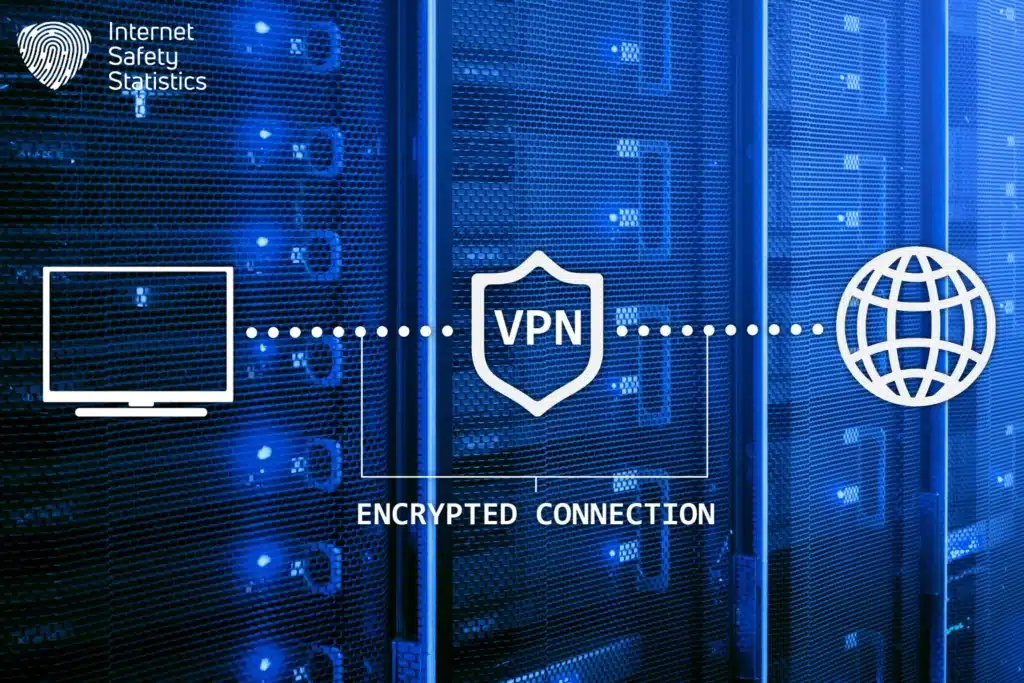
Does VPN Encrypt Data?
A VPN does encrypt data. When you use a VPN, the internet traffic is usually routed through a secure and encrypted connection to a server, which is operated by the VPN provider. This process helps protect your data from being intercepted by third parties, such as hackers or your Internet Service Provider (ISP). Here’s how the encryption process works with a VPN:
1. Tunnelling: A VPN creates a secure tunnel between your device and the VPN server. This tunnel is encrypted, preventing anyone from eavesdropping on your internet activities.
2. Encryption Protocols: VPNs use various encryption protocols to secure the data within the tunnel. Common protocols include OpenVPN, L2TP/IPSec, and IKEv2/IPSec.
3. Data Protection: Once your data is within the encrypted tunnel, it becomes much more difficult for unauthorised parties to access or decipher; this is essential when using public Wi-Fi networks or when you want to maintain privacy while browsing the Internet.
For complete data security, it’s recommended to use other encryption methods like HTTPS for websites and additional tools for encrypting local files if needed. Additionally, choosing a reputable and trustworthy VPN provider is crucial for ensuring the effectiveness of the encryption.
How Do You Encrypt Data Without a VPN?
If you’re looking to encrypt specific files or communications without using a VPN, there are several other methods you can explore:
1. Use End-to-End Encryption (E2EE): Services like Signal for messaging or ProtonMail for email provide end-to-end encryption.
2. File Encryption Software: Tools like VeraCrypt or BitLocker (for Windows) allow you to encrypt entire drives or create encrypted containers for specific files. You can use these tools to protect sensitive data on your computer.
3. Secure Socket Layer (SSL) and Transport Layer Security (TLS): These protocols encrypt data in transit on the Internet. Many websites use HTTPS (HTTP Secure) to ensure secure and protected communication between browsers and websites.
4. SSH (Secure Shell) for Remote Access: SSH provides a secure, encrypted connection if you access a remote server.
5. PGP (Pretty Good Privacy): PGP is a data encryption and decryption program that delivers cryptographic privacy and authentication for data communication; you can use it to encrypt emails or files.
How Is Internet Data Encrypted?
Internet data can be encrypted using various protocols and technologies to ensure privacy and security. Here are a few key methods:
1. SSL/TLS
Secure Sockets Layer/Transport Layer Security protocols are commonly used to secure data transmitted between a user’s web browser and a website. When you see “https://” in a URL, it indicates that the connection is encrypted using SSL/TLS. This encryption ensures that the exchanged data, such as login credentials or personal information, is secure.
2. VPN
A VPN encrypts the internet connection by creating a secure path between the device and the VPN server; this prevents third parties, like hackers or your ISP, from monitoring your online activities. VPNs use protocols like OpenVPN, IPSec, or L2TP/IPSec to establish this encrypted connection.
3. E2EE
The end-to-end encryption technique ensures that only the sender and the recipient can see the data. It’s commonly used in messaging apps like Signal and WhatsApp. Even if the data travels through servers, it remains encrypted, and only the endpoints (sender and receiver) have the necessary keys to decrypt it.
4. SSH
SSH (Secure Shell) is a cryptographic network protocol that delivers a secure way to access and manage network devices remotely. It encrypts the client and server communication, preventing unauthorised access and eavesdropping.
5. PGP
PGP (Pretty Good Privacy) is a data encryption and decryption program that delivers cryptographic privacy and authentication for data communication.
All these methods use encryption algorithms and key exchange mechanisms to protect data in transit, making it difficult for unauthorised parties to interpret the information.
How Do You Encrypt an IP Address?
Encrypting an IP address isn’t a standard practice because IP addresses are used for routing data on the Internet, and encrypting them would interfere with the basic functioning of the network. However, using a VPN is a good idea if you’re concerned about privacy and want to cover your IP address. Here’s how a VPN works to help keep your IP address private:
1. VPN Connection: After connecting to a VPN, the internet traffic is usually routed through a secure server operated by the VPN provider.
2. IP Address Masking: Instead of using your real IP address, the VPN server assigns you a different IP address; this is the IP address that websites and online services see, adding a layer of anonymity.
3. Encryption: The data transmitted between your device and the VPN server is encrypted, making it difficult for third parties to intercept and decipher.
Keep in mind that while a VPN provides a level of privacy, it doesn’t make your IP address completely invisible. The VPN provider knows your real IP address, and you should choose a reputable provider that values your privacy. Remember that using a VPN is just one aspect of online privacy. Be aware of your services’ privacy policies and adopt good security practices to protect your online activities.
How To Encrypt Your Wi-Fi?

Encrypting your Wi-Fi network adds a layer of security to prevent unauthorised access. Here’s how to encrypt your Wi-Fi:
1. Access Your Router Settings: Open a web browser and write your router’s IP address in the address bar. Common addresses are 192.168.1.1 or 192.168.0.1. Check your router’s manual or the manufacturer’s website for the correct address.
2. Login to Your Router: Enter your router’s username and password. If you need to modify them from the default values, see the router handbook for the default credentials.
3. Find the Wireless Security Settings: Look for a section related to wireless or Wi-Fi settings. There should be an option for “Wireless Security”, “Security”, or something similar.
4. Choose a Security Protocol: Select WPA3 (Wi-Fi Protected Access 3) if your router and devices support it. If not, WPA2 is still secure, but avoid using WEP (Wired Equivalent Privacy) as it is outdated and less secure.
5. Set a Strong Passphrase: Create a strong, unique passphrase for your Wi-Fi network. Aim for a mix of upper and lowercase letters, numbers, and symbols. The longer and more complex, the better.
6. Save Changes: After applying the changes, your router will restart, and your Wi-Fi network will be encrypted.
7. Update Other Devices: Once your Wi-Fi is encrypted, you must update the Wi-Fi settings on all your connected devices. Enter the new passphrase to regain access.
Encrypting your Wi-Fi protects your network from unauthorised access and secures the data transmitted between your devices and the router. It’s a crucial step in maintaining a secure home network.
Can Public Wi-Fi Be Encrypted?
Public Wi-Fi networks can also be encrypted to secure the data transmitted over them. However, the encryption is typically set up by the network administrator or service provider, not the individual user. When you connect to a public Wi-Fi network, checking for encryption is essential to ensure a secure connection. Here are common types of encryption used on public Wi-Fi networks:
1. WPA2/WPA3 (Wi-Fi Protected Access): Many modern public Wi-Fi networks secure the connection using WPA2 or WPA3 encryption. The same encryption is used for home Wi-Fi networks.
2. WEP (Wired Equivalent Privacy): Although outdated and less secure, some older public Wi-Fi networks may still use WEP encryption. It’s vulnerable to security breaches, and you should avoid connecting to networks using WEP.
3. Captive Portals: Public Wi-Fi networks occasionally employ captive portals, which are websites that demand users log in or accept terms before allowing them to access the Internet. While this is not encryption, it adds a layer of authentication.
When connecting to public Wi-Fi, look for networks that require a password, which often indicates some level of encryption. Avoid connecting to open, unsecured networks without any password or authentication requirements. Public Wi-Fi networks can still pose security risks even with encryption. Practising good security habits, such as avoiding sensitive transactions and using a VPN when connecting to unfamiliar networks, is essential.
Can a Hacker See Encrypted Data?
While it’s incredibly challenging for a hacker to decipher encrypted data directly, it’s not entirely impossible. Here are a few factors to consider:
1. Encryption Strength: Modern encryption algorithms, such as AES (Advanced Encryption Standard), are considered secure. However, if a hacker discovers a vulnerability or flaw in the algorithm, it could compromise the encryption.
2. Key Length and Complexity: Longer and more complex encryption keys provide higher security. Using longer key lengths for better resistance against brute-force attacks is recommended as technology advances.
3. Brute-Force Attacks: A brute-force attack involves attempting all possible combinations of keys until the correct one is found. Strong encryption and longer key lengths significantly increase the time and computational power required for a successful brute-force attack.
4. Side-Channel Attacks: Some attacks don’t directly target the encryption algorithm but exploit weaknesses in the implementation or other side channels. These could include timing attacks, power consumption analysis, or other methods to gain information about the encryption key.
5. Endpoint Security: Even if data is encrypted during transmission, it must be decrypted at the endpoints (e.g., your device and the server). If a hacker gains access to these endpoints or compromises the involved devices, they might be able to access decrypted data.
Using reputable encryption protocols, keeping software up to date, and following best security practices are crucial to maintaining the integrity of encrypted data.
What Is the Best Encryption for Home Internet?
The best encryption protocols for Wi-Fi networks for securing your home internet are WPA3 (Wi-Fi Protected Access 3) and WPA2 (Wi-Fi Protected Access 2). Here’s a brief overview of each:
WPA3
WPA3 is the latest Wi-Fi security protocol, providing stronger encryption and better protection against attacks than its predecessor, WPA2. It includes individualised data encryption, protection against brute-force attacks, and improved security for devices with limited display capabilities (IoT devices).
WPA2
WPA2 has been widely used and considered secure for many years. It uses the Advanced Encryption Standard (AES) for data encryption, providing a strong level of security. While WPA2 is still secure, it’s recommended to use WPA3 if your devices and router support it, as it offers additional security enhancements.
Set Up WPA3 or WPA2
To set up WPA3 or WPA2 encryption on your home Wi-Fi network, follow these instructions:
1. Access your router settings through a web browser by entering the router’s IP address.
2. Navigate to the wireless or Wi-Fi settings section.
3. Look for the security settings and choose WPA3 or WPA2, depending on your preferences and device compatibility.
4. Set a strong passphrase for your Wi-Fi network.
Always use a unique and strong passphrase for your Wi-Fi network to add an extra layer of security. Keep your router’s firmware current to ensure you have the latest security patches.
As we navigate the vast expanses of the digital universe, the need to safeguard our online activities becomes non-negotiable. Encrypting your internet connection is not merely a precaution; it’s an essential practice in the age of constant connectivity. Embrace the power of encryption, fortify your digital fortress, and confidently navigate the online realm, knowing your data is secure against the currents of the ever-evolving digital landscape.
