
One vital component of a robust security setup is a firewall—a barrier that acts as a first line of defence against unauthorised access and malicious activities. Avast Firewall is a trusted and widely-used option among the numerous firewall solutions available.
Avast Firewall, developed by the renowned cybersecurity company Avast, offers comprehensive protection by monitoring and controlling network traffic to and from your computer. By understanding how to configure Avast Firewall effectively, you can allow specific programs or applications to communicate with the network, striking a balance between security and functionality.
Avast Firewall
Before delving into the intricacies of allowing a program through Avast Firewall, it is crucial to grasp the fundamental concepts behind firewalls and their purpose. A firewall is a barrier between your computer and external networks, monitoring incoming and outgoing network traffic based on predefined security rules.
Avast Firewall furthers this concept by providing robust features to safeguard your system. It constantly analyses network communications and employs advanced algorithms to identify potential threats. By enforcing network traffic rules, Avast Firewall ensures that only authorised and safe connections are established, preventing unauthorised access to your computer and sensitive data.
Some of the key features offered by Avast Firewall include packet filtering, application control, and network intrusion detection. Packet filtering involves examining individual network packets to determine if they should be allowed or blocked based on predetermined rules. Application control enables you to manage network access permissions for specific programs or processes. Network intrusion detection actively monitors network traffic for signs of suspicious or malicious activity, providing additional protection.
Using Avast Firewall’s comprehensive suite of tools, you can protect your computer from unauthorised access, data breaches, and other potential threats.
Identifying the Program to Be Allowed
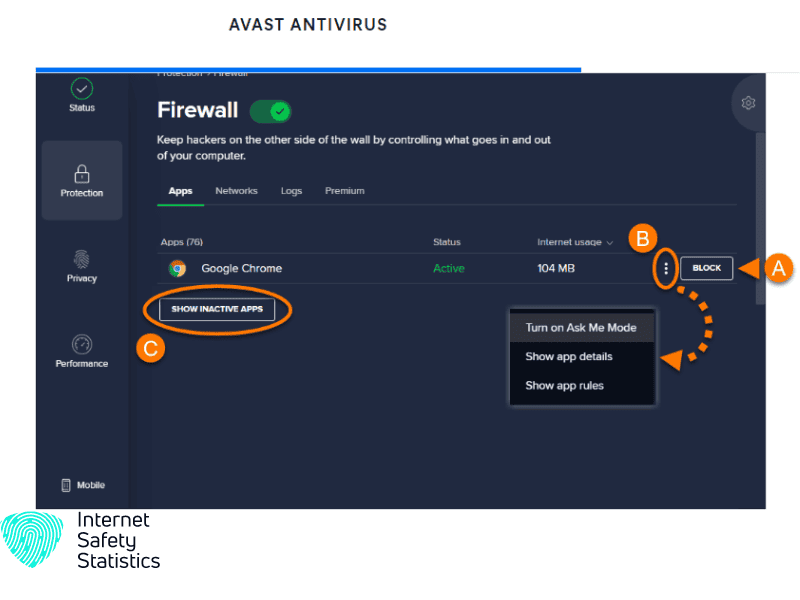
Before you can proceed with configuring Avast Firewall to allow a program through its protective barriers, you must first identify the specific program or application that requires network access. There are several scenarios in which you may need to allow a program through the firewall:
- Custom or third-party applications: If you have installed a custom or third-party application that requires internet connectivity, such as a specialised software tool or an online game, you must grant access through Avast Firewall.
- Communication software: Programs like instant messaging applications, video conferencing tools, or Voice-over-IP (VoIP) clients rely on network connectivity for their core functionality. If you use any of these communication tools, you may need to configure Avast Firewall to permit their network access.
- File sharing applications: Such applications allow sharing of digital files across the network. These Peer-to-peer (P2P) file-sharing applications, such as BitTorrent clients or file transfer protocols, often require unrestricted network access, which can be disrupted by an Avast firewall. You’ll need to let these applications through the firewall in order to use them.
You can configure the firewall settings once you have identified the program or application that must be allowed through Avast Firewall.
Configuring Avast Firewall Settings
Configuring Avast Firewall to allow a program through its protective shield involves accessing the firewall settings and making the necessary adjustments. Follow these steps:
- Launch Avast: Start by opening the Avast user interface on your computer. You can typically find the Avast icon in the system tray or search for it in the Start menu.
- Access the Firewall settings: You can access the firewall settings by navigating to the “Protection” or “Security” section. Remember, each version of the software may have different settings.
- Open the Firewall settings: Once you have located them, click on them to access the configuration options. This will open up a window where you can manage the firewall rules and settings.
Take some time to familiarise yourself with the various options and sections available in the firewall settings. Avast Firewall offers a range of configuration options, including network profiles, application rules, and packet rules, among others. Understanding these settings will help you make informed decisions while configuring Avast Firewall to allow a program through its defences.
Remember, configuring firewall settings may vary slightly based on the version of Avast Firewall you have installed on your computer. However, the core concepts and steps outlined here will provide a general guideline.
Creating a New Firewall Rule
Once you have accessed the firewall settings in Avast, you can create a new rule to allow the specific program through the firewall. Follow these step-by-step instructions to configure Avast Firewall and permit network access for the desired program:
- Specify the program or application: Within the Firewall settings, locate the section for creating application rules or exceptions. Click on the option to add a new rule or exception.
- Identify the program: In the rule creation window, you will typically find an option to browse and select the program or application you want to allow through the firewall. Browse your computer’s directories and select the executable file or process associated with the program.
- Define network ports or protocols: Depending on the program’s requirements, you may need to specify network ports or protocols for inbound and outbound connections. Refer to the program’s documentation or contact the software provider to gather the necessary information. Enter the port numbers or protocols accordingly.
- Select the rule action: Choose whether to allow or block the program’s network access. In this case, you would select “Allow” to grant the program permission to communicate over the network.
- Set additional conditions or exceptions (if applicable): Avast Firewall may offer options to set different conditions or exceptions for the rule. For example, you can specify trusted networks, time restrictions, or advanced filtering criteria. Adjust these settings based on your specific requirements.
- Save the rule: After configuring all the necessary settings, save the firewall rule. Avast Firewall will now apply the rule and permit the program to access the network.
Testing and Verifying the Firewall Rule
After creating the firewall rule, testing and verifying that the program can now successfully communicate over the network is essential. Follow these steps to ensure that the rule is functioning as intended:
- Restart the program: Close and reopen the program you allowed through Avast Firewall. This step ensures that the program initiates a new network connection, triggering the firewall rule to come into effect.
- Test network connectivity: Use the program’s features or functionalities that require network access. For instance, try accessing a website if it is a web browser. If it is a chat application, attempt to send a message. Verify that the program can establish the necessary network connections without any disruptions.
- Monitor firewall logs: Avast Firewall typically keeps records of its activities. Check the firewall logs to ensure the program’s network connections are allowed according to the rule you created. If you encounter any issues or unexpected behaviour, consult the firewall logs for potential error messages or blocked connections.
- Troubleshoot if necessary: If the program still faces network connectivity issues, double-check the firewall rule settings, including the specified ports, protocols, and exceptions. Make any necessary adjustments and repeat the testing process. Additionally, ensure that any other security software or network configuration does not block the program.
By thoroughly testing and verifying the firewall rule, you can ensure the program can freely communicate over the network while benefiting from Avast Firewall’s protection.
Managing Existing Firewall Rules
Periodic review and management of firewall rules are crucial to maintaining an optimal security posture. Avast Firewall offers features to manage existing laws effectively. Here are some key points to consider:
- Modifying rules: If you need to change the settings or parameters of an existing rule, access the Firewall settings in Avast and locate the rule you wish to modify. Edit the rule according to your requirements and save the changes.
- Deleting rules: In case a program or application no longer requires network access, or if you want to revoke access, you can delete the corresponding firewall rule. Find the rule you want to remove and delete within the firewall settings.
Regularly reviewing and managing firewall rules will ensure your network remains secure while accommodating changes in program requirements.
Maximise Your Security
When configuring Avast Firewall or any firewall solution, following best practices to maximise security is essential. Consider the following recommendations:
- Regular updates: Keep Avast Firewall and all related security software updated all the time. Regular updates patch vulnerabilities and provide essential security enhancements.
- Principle of least privilege: Only allow network access for programs or applications requiring it. Minimise the number of firewall rules and exceptions to reduce the attack surface.
- Use trusted sources: Obtain programs and applications from reputable sources to minimise the risk of installing malicious software.
- Monitor firewall logs: Regularly review their f logs for suspicious activities, blocked connections, or unauthorised access attempts.
- Combine with other security measures: Avast Firewall is just one component of a comprehensive security strategy. Use it with other security measures like antivirus software, safe browsing practices, and strong passwords.
Adhering to these best practices can fortify your network defences and protect your computer and data from potential threats.
Configuring a firewall, such as Avast Firewall, to allow a program through its protective barriers is essential to maintaining a secure and functional computing environment. In this article, we explored the process of letting a program through Avast Firewall, beginning with identifying the program and configuring the firewall settings accordingly. Remember, a robust firewall configuration is part of a comprehensive security strategy. Stay informed about emerging threats, keep your software up to date, and maintain good cybersecurity practices to ensure the ongoing protection of your computer and network.
