
In the ever-evolving landscape of cybercrime, a new and dangerous trend is emerging: Cybercrime-as-a-Service (CaaS). This illegal model offers cybercriminals the tools, resources, and expertise to launch sophisticated attacks on businesses, making it a looming threat that organisations cannot afford to ignore. This article explores the rise of CaaS and its potential implications for businesses, emphasising the importance of proactive measures to mitigate the risks.
Understanding Cybercrime-as-a-Service
Cybercrime-as-a-Service (CaaS) refers to the commercialisation and provision of cyber criminal tools, services, and infrastructure by cybercriminals to other individuals or groups. It operates on a similar model to Software-as-a-Service (SaaS) or Platform-as-a-Service (PaaS) in the legitimate technology industry. CaaS allows individuals with limited technical skills to engage in cybercriminal activities by renting or purchasing various malicious tools, such as malware, exploit kits, phishing kits, botnets, and hacking services.
CaaS providers offer a range of illicit services, including but not limited to distributed denial-of-service (DDOS) attacks, email and social media account hacking, credit card fraud, ransomware attacks, and stolen data trading. These services are typically advertised and accessed through underground forums, dark web marketplaces, or private networks.
The rise of CaaS has lowered the entry barrier for aspiring cyber criminals, enabling them to access sophisticated attack tools and infrastructure without extensive technical knowledge. CaaS has led to an increase in the scale and complexity of cybercrime, as it allows malicious actors to operate more efficiently and on a global scale.
The consequences of CaaS are far-reaching, affecting individuals, businesses, and even governments. It poses significant challenges for law enforcement agencies and cybersecurity professionals as the distribution and coordination of cybercriminal activities become decentralised and more difficult to trace.

To combat the proliferation of CaaS, a collaboration between law enforcement, cybersecurity organisations, and technology companies is crucial. Increased awareness, proactive threat intelligence sharing, and the development of advanced detection and mitigation strategies are essential to mitigate the risks associated with CaaS and protect against evolving cyber threats.
In the context of Cybercrime-as-a-Service (CaaS), the point “Service Offerings” refers to the wide range of illicit services that are available within the CaaS ecosystem. These services are provided by cybercriminals to other individuals or groups who seek to engage in malicious activities. Here are some examples of the specific services found in the CaaS landscape:
Within the CaaS ecosystem, these service offerings create a thriving marketplace where cybercriminals can access and leverage various tools and resources to carry out their malicious activities. The availability of these services lowers the entry barrier for aspiring cybercriminals, allowing them to engage in sophisticated cyberattacks without needing to develop their own tools or expertise.
It is important to note that discussing these services does not endorse or promote any illegal activities. Understanding the existence and nature of these services is essential for cybersecurity professionals, law enforcement agencies, and organisations to stay informed about the evolving threats and develop effective countermeasures to protect against cybercrime.
Types of CaaS
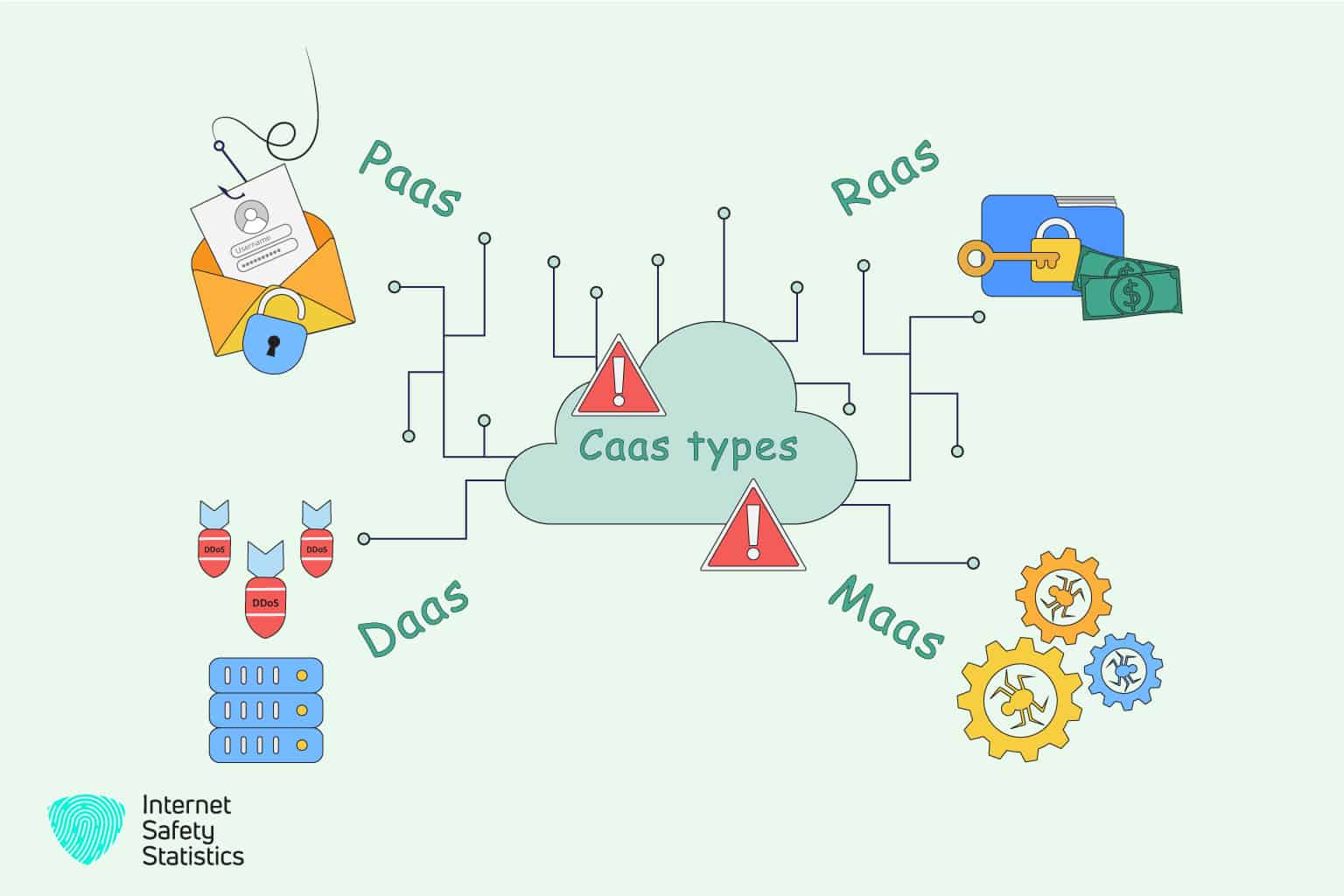
Cybercrime-as-a-Service (CaaS) encompasses various types of illicit services that are offered by cybercriminals to individuals or groups seeking to engage in cybercriminal activities. Here are some of the common types of CaaS:
Malware-as-a-Service (MaaS)
MaaS involves the provision of ready-made or custom-built malware by cybercriminals. It includes a wide range of malicious software such as viruses, worms, Trojans, ransomware, spyware, or keyloggers. Cybercriminals can purchase or rent these malware strains to launch attacks on unsuspecting victims.
Ransomware-as-a-Service (RaaS)
RaaS is a specialised form of CaaS where cybercriminals offer ransomware tools and infrastructure to other individuals or groups in exchange for a share of the profits. This service allows non-technical individuals to launch ransomware attacks, encrypting victims’ files and demanding a ransom in exchange for decryption.
This form of cybercrime has gained significant traction due to its ease of use, accessibility, and potential for financial gain. RaaS allows aspiring cybercriminals with limited technical skills to launch ransomware attacks without having to develop the malware themselves.
These aspiring criminals can simply purchase or rent the ransomware from the RaaS provider and customise it to their specific targets. The RaaS provider typically takes care of the infrastructure, such as command-and-control servers and payment systems, while also providing support and guidance. This business model has democratised ransomware attacks, leading to an increase in their frequency and sophistication. Organisations must remain vigilant and implement robust cybersecurity measures to protect themselves from the ever-evolving threat of Ransomware-as-a-Service.
DDoS-as-a-Service (DaaS)
DaaS provides distributed denial-of-service (DDoS) attack capabilities to customers. Cybercriminals offer access to botnets or networks of compromised devices, which can be used to overwhelm a target’s systems or websites with a massive volume of traffic, causing disruptions or service outages.
Phishing-as-a-Service (PhaaS)
This is a dangerous cybercriminal offering that provides individuals or groups with the necessary tools and infrastructure to carry out phishing attacks. PhaaS simplifies the process of executing phishing campaigns by offering pre-designed templates, email content customisation, and targeted industry selection.
It allows even those with limited technical expertise to launch effective phishing attacks. PhaaS providers often offer command-and-control infrastructure, compromised systems, and access to botnets, enabling the widespread distribution of phishing emails and the hosting of deceptive phishing websites.
This illicit service poses a significant threat to individuals and organisations as it facilitates the theft of sensitive information such as login credentials, financial details, and personal data. PhaaS emphasises the need for robust security measures, user awareness, and continuous education to mitigate the risks associated with phishing attacks.
It allows even those with limited technical expertise to launch effective phishing attacks. PhaaS providers often offer command-and-control infrastructure, compromised systems, and access to botnets, enabling the widespread distribution of phishing emails and the hosting of deceptive phishing websites.
This illicit service poses a significant threat to individuals and organisations, as it facilitates the theft of sensitive information such as login credentials, financial details, and personal data. PhaaS emphasises the need for robust security measures, user awareness, and continuous education to mitigate the risks associated with phishing attacks.
Hacking Services
Cybercriminals offer hacking services, including website hacking, social media account compromise, email hacking, or network intrusions. These services cater to individuals or groups seeking unauthorised access to specific targets for various purposes.
Credential Theft and Sale
CaaS platforms often facilitate the sale and exchange of stolen credentials, including usernames, passwords, credit card information, or other personal data. Cybercriminals can purchase these stolen credentials to carry out identity theft and financial fraud or gain unauthorised access to online accounts.
Exploit Kits
Exploit kits are tools that target software vulnerabilities to deliver malware or gain unauthorised access to systems. CaaS providers offer exploit kits, allowing individuals without deep technical knowledge to exploit software vulnerabilities and launch attacks against vulnerable targets.
Carding and Fraud Services
CaaS platforms also cater to carding and fraud services. This involves the sale and exchange of stolen credit card information, carding tutorials, or services related to fraudulent financial activities, such as money laundering or ATM skimming.
Crypting Services
Crypting services involve the modification and obfuscation of malware to evade detection by security software. CaaS providers offer encryption and crypting services to cybercriminals, enabling them to create undetectable malware that can bypass traditional security measures.
Stolen Data Marketplaces
CaaS platforms may include marketplaces where cybercriminals buy and sell stolen data, such as credit card information, login credentials, personal identifiable information (PII), or financial records. These marketplaces act as hubs for trading stolen data, allowing cybercriminals to profit from their illicit activities.
These are just a few examples of the types of CaaS available in the cybercriminal underground. It is important to note that discussing these types of services does not endorse or promote any illegal activities. Understanding the existence and nature of these services is crucial for cybersecurity professionals and law enforcement agencies to develop effective countermeasures and protect against cyber threats.
Why Did Cybercrime-as-a-Service Arise?

Cybercrime-as-a-Service (CaaS) has emerged as a result of several factors that have shaped the cybersecurity landscape. The following are key reasons behind the rise of CaaS:
- Monetisation of Cybercrime: Cybercriminals have realised the potential for substantial financial gain through illicit activities. CaaS provides them with a means to profit from their skills and resources by offering cybercrime tools, services, and expertise to other malicious actors.
- Specialisation and Expertise: Cybercrime has become increasingly complex and requires specialised knowledge in various areas, such as malware development, exploit creation, or data theft. CaaS allows cybercriminals to specialise in specific aspects of cybercrime and offer their expertise as a service to those lacking the necessary skills or resources.
- Lower Barrier to Entry: Traditionally, engaging in sophisticated cybercrime required significant technical expertise, infrastructure, and resources. CaaS lowers the entry barrier by providing ready-made tools and services that can be easily accessed and used by individuals with limited technical knowledge, amplifying the potential pool of cybercriminals.
- Globalisation and Connectivity: The interconnected nature of the internet has facilitated the proliferation of CaaS. Malicious actors from different parts of the world can connect and collaborate through underground forums, marketplaces, and encrypted communication channels, enabling the exchange of CaaS offerings and expertise on a global scale.
- Anonymity and Evading Law Enforcement: CaaS operations often operate in the dark web or other hidden corners of the internet, allowing cybercriminals to maintain anonymity and evade law enforcement. This anonymity provides a sense of security for criminals, making it more difficult to trace and apprehend them.
- Profitability and Reduced Risk: CaaS offers a lucrative business model for cybercriminals. By providing services and tools rather than directly carrying out attacks, they can generate income while reducing their personal risk of being caught or identified. This shift in approach allows them to profit from cybercrime while minimising their exposure to law enforcement efforts.
- Rapid Technological Advancements: Advancements in technology, such as cryptocurrency and anonymisation techniques, have further facilitated CaaS operations. Cryptocurrencies provide anonymous and untraceable payment methods, making transactions within the CaaS ecosystem more secure and less susceptible to detection.
In summary, the rise of CaaS is driven by the desire for financial gain, the specialisation of cybercrime, accessibility, global connectivity, anonymity, and technological advancements. Understanding these factors is crucial for combating CaaS effectively and developing robust cybersecurity strategies to protect individuals and organisations from its threats.
Why Is CaaS Dangerous?
Cybercrime-as-a-Service (CaaS) poses significant dangers due to its accessibility, sophistication, global reach, collaborative nature, and monetisation of cybercrime. CaaS lowers the entry barrier, allowing more individuals to access advanced tools and services for conducting cyberattacks. The collaborative environment enables the rapid evolution of attack techniques.
With a global reach, cybercriminals can target victims worldwide while evading law enforcement through anonymising technologies. The monetisation of cybercrime incentivises its growth. Overall, CaaS contributes to an ever-evolving threat landscape, making it crucial for individuals, governments, and businesses to take proactive measures to protect themselves from this dangerous phenomenon.
How Can Organizations Protect Themselves From CaaS?
Organisations can take several measures to protect themselves from Cybercrime-as-a-Service (CaaS) threats. Here are some key steps to consider:
Strengthen Cybersecurity Infrastructure
Implement robust cybersecurity measures, including firewalls, intrusion detection systems, and antivirus software to protect against CaaS attacks. Regularly update and patch systems to address vulnerabilities.
Employee Education and Awareness
Train employees on cybersecurity best practices, including recognising phishing emails, practising strong password hygiene, and avoiding suspicious websites or downloads. Create a culture of security awareness throughout the organisation.
Multi-Factor Authentication (MFA)
Implement MFA for critical systems and applications to provide an additional layer of protection. This helps mitigate the risk of stolen credentials being used in CaaS attacks.
Regular Security Assessments
Conduct regular security assessments and penetration testing to identify vulnerabilities and address them promptly. Stay informed about the latest threats and ensure security measures are up to date.
Incident Response Planning
Develop a comprehensive incident response plan to respond to CaaS attacks effectively. This includes steps for containment, eradication, and recovery. Regularly test and update the plan to ensure its effectiveness.
Vendor Risk Management
Assess the security practices of third-party vendors and partners. Ensure that they have appropriate security measures in place and adhere to industry best practices to minimise the risk of CaaS-related incidents.
Threat Intelligence Sharing
Collaborate with industry peers and share threat intelligence information to stay informed about emerging CaaS trends and tactics. Engage in information-sharing platforms or join industry-specific cybersecurity forums.
Data Backup and Recovery
Implement regular data backup procedures to ensure business continuity in the event of a CaaS attack. Test data restoration processes to ensure the integrity and availability of critical data.
Employee Privilege Management
Implement the principle of least privilege, granting employees access only to the systems and data necessary for their roles. Regularly review and update access permissions to minimise the risk of unauthorised access.
Proactive Monitoring and Response
Implement continuous monitoring solutions, including intrusion detection systems and security information and event management (SIEM) tools. Monitor network traffic, user behaviour, and system logs to detect and respond to CaaS-related incidents promptly.
By adopting a proactive and comprehensive approach to cybersecurity, organisations can significantly reduce their risk of exposure to CaaS threats. It is crucial to regularly reassess and update security measures to stay ahead of evolving cyber threats.
