Ransomware attacks have become increasingly prevalent in today’s digital landscape, causing significant disruptions and financial losses for individuals and organisations. When confronted with a ransomware attack, it is crucial to have a comprehensive recovery plan in place to minimise the impact and ensure the restoration of vital data and systems. This article provides valuable insights into effective ransomware recovery strategies, preventative measures, and best practices for data recovery in the event of a ransomware incident.
What is a Ransomware Attack?
Ransomware is a type of malicious software designed to deny access to a computer system or data until a ransom is paid. It typically encrypts the victim’s files or locks the screen to prevent access to the data. Once the ransom is paid, the attacker may or may not provide the decryption key to restore access. They are often carried out through phishing emails, exploit kits, or malicious attachments.
Types of Ransomware Attacks
There are many different types of ransomware, but they can be broadly divided into two main categories:
Crypto-ransomware: This is the most common type of ransomware. It encrypts the victim’s files and holds them hostage until the victim pays a ransom. It typically uses strong encryption algorithms that are difficult to crack, making it challenging for victims to decrypt their files without paying the ransom.
Locker-ransomware: This type does not encrypt files. Instead, it locks up the victim‘s computer or device, preventing them from accessing their files or using the device. It typically demands a ransom payment to unlock the device.
Here are some of the most common types of ransomware:
- Petya: Petya is a type of locker ransomware that first appeared in 2016. It is known for its ability to encrypt the Master Boot Record (MBR) of a computer, which can make it very difficult to recover.
- Ransomware-as-a-Service (RaaS): RaaS is a business model that allows cybercriminals to rent out ransomware to other cybercriminals. This makes it easier for cybercriminals to deploy ransomware without having to develop their own code.
- Double extortion ransomware: This type of ransomware not only encrypts files but also steals sensitive data from the victim’s computer. The cybercriminals then threaten to release the stolen data if the victim does not pay the ransom.
- Zero-day ransomware: Zero-day ransomware is a type that exploits vulnerabilities that are not yet known to the public. This makes it very difficult to defend against, as there are no patches available to fix the vulnerabilities.
Ransomware Recovery
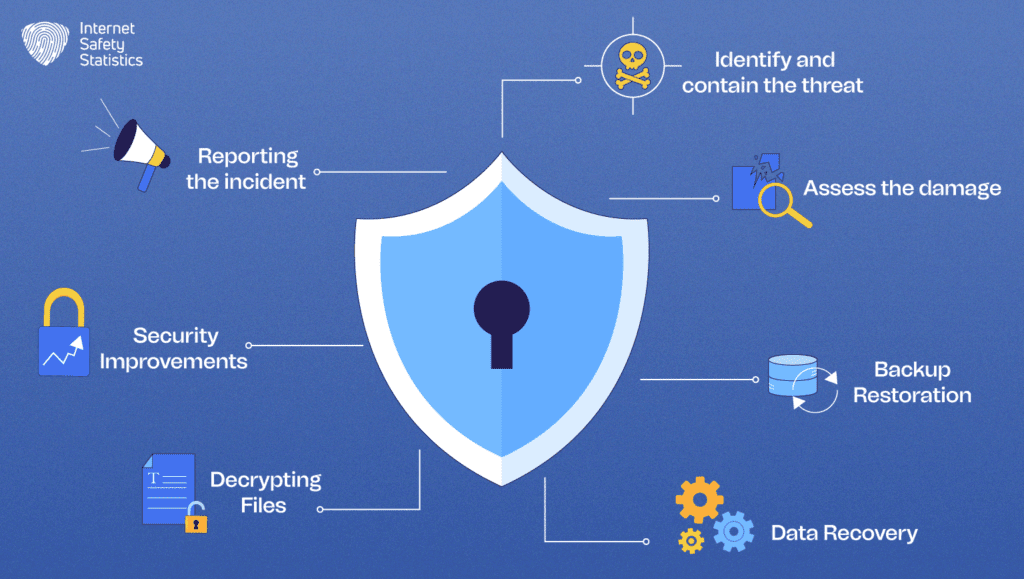
Recovering from a ransomware attack can be a challenging and complicated process, but several steps can be taken to minimise the impact and restore systems and data:
- Identify and contain the threat: If the attack is suspected, immediately isolate the affected systems from the network to prevent further spread of the infection. This can help contain the damage and prevent additional data loss.
- Assess the damage: Evaluate the extent of the damage caused by such an attack, including the systems and data affected. This will help determine the scope of the recovery effort and prioritise which systems and data need to be restored first.
- Backup restoration: If backups of the affected systems and data are available, they should be used to restore the affected systems to their pre-attack state. It’s important to ensure that the backup copies are not infected with ransomware before restoring them.
- Data recovery: In cases where backups are not available or are insufficient, data recovery tools and techniques may be used to attempt to recover encrypted or deleted files. This can be a complex and time-consuming process, but it may be necessary to recover critical data.
- Decrypting files: In some cases, decryption tools provided by cybersecurity firms or law enforcement agencies may be available to recover files encrypted by ransomware. These tools can be used to attempt to unlock the encrypted data without paying the ransom.
- Security improvements: Once the affected systems have been restored, it’s important to implement security improvements to prevent future attacks. This may include updating and patching software, implementing stronger access controls, and providing cybersecurity awareness training to staff.
- Reporting the incident: It’s important to report the ransomware attack to law enforcement and regulatory authorities, as well as any relevant industry organisations. This can help track and stop the attackers, as well as fulfil legal and compliance requirements.
Recovering from a ransomware attack can be a lengthy and challenging process, but with the right approach and support, it is possible to restore systems and data and improve the organisation’s cybersecurity posture.
When an attack occurs, the immediate focus is on initiating a robust ransomware recovery plan to mitigate the damage and restore normal operations. Effective strategies for recovery involve timely identification of the attack, isolating infected systems, and deploying data backup and restoration processes to recover encrypted files and critical information.
Creating a recovery plan for ransomware attacks is essential for organisations to streamline their response efforts and minimise the impact of the incident. Best practices to recover from ransomware entail maintaining regular data backups, implementing continuous data protection measures, and establishing secure data recovery protocols to ensure rapid restoration of vital information.
Strategies for Ransomware Recovery
Data Backups: Importance and Methods for Maintaining Secure Backups
Data backups are crucial for recovering from ransomware attacks. By having a copy of your data that is stored offsite, you can restore your systems and data if they are encrypted by ransomware. There are two main types of data backups:
- Full backups: These backups copy all of the data on your system to a secure location.
- Incremental backups: These backups only copy the data that has changed since the last full backup.
It is recommended that you have at least two copies of your data, one on-site and one off-site. The on-site backup should be stored in a secure location, such as a fireproof safe or a secure server room. The off-site backup should be stored in a different location, such as a cloud storage service or a secondary data centre.
In addition to regular backups, it is also important to test your backups regularly to ensure that they are working properly. This will help you to ensure that you can restore your data if you are attacked by ransomware.
Utilising Ransomware Decryption Tools (if available and recommended)
In some cases, it may be possible to decrypt your files using a ransomware decryption tool. These tools are typically developed by security researchers or law enforcement agencies. However, it is important to note that not all ransomware attacks can be decrypted, and even if a decryption tool is available, it may not work for your particular ransomware variant.
Before attempting to decrypt your files using a ransomware decryption tool, it is important to consult with a cybersecurity professional to ensure that the tool is safe and that it will not damage your data further.
Seeking Assistance from Cybersecurity Professionals for Recovery
If you are the victim of a ransomware attack, it is important to seek assistance from a cybersecurity professional as soon as possible. Cybersecurity professionals can help you to identify the variant that you have been infected with, assess the damage, and develop a recovery plan.
Steps for Ransomware Attack Prevention

Such attacks can be devastating for businesses, as they can lead to data loss, downtime, and reputational damage.
Here are some tips on how to prevent ransomware attacks:
- Create and enforce strong password policies: Strong passwords are the first line of defence against cyberattacks. To create a robust password policy, organisations should:
- Require strong passwords: Passwords should be at least 12 characters long and include a mix of upper and lowercase letters, numbers, and symbols.
- Prohibit common passwords: Common passwords, such as keyboard patterns or personal information, should be prohibited.
- Enforce password expiration: Passwords should expire regularly, requiring employees to change them periodically.
- Implement multi-factor authentication (MFA): MFA adds an extra layer of security by requiring two or more pieces of verification, such as a password and a code sent to a mobile phone. This makes it much more difficult for attackers to gain unauthorised access, even if they have stolen a user’s password.
- Regularly update software and patches: Software updates often contain patches that fix vulnerabilities that attackers can exploit. Regular software updates are essential to stay ahead of the latest security threats. This includes:
- Automating software updates: Organisations should automate software updates to ensure that they are installed promptly.
- Providing employee training: Employees should be trained on how to install updates manually.
- Testing updates before deployment: Organisations should test updates in a test environment before deploying them to production.
- Implement data loss prevention (DLP): DLP software helps to prevent sensitive data from accidentally or intentionally leaking from the organisation. DLP software can monitor email, file sharing, and other data transfer methods to identify and prevent the unauthorised transmission of sensitive data.
- Conduct regular penetration tests: Penetration testing is a simulated cyberattack that helps organisations identify and fix vulnerabilities in their security systems. By conducting regular penetration tests, organisations can stay ahead of the curve and take steps to patch vulnerabilities before they can be exploited by real hackers.
- Maintain comprehensive data backups: Data backups are essential for recovering from a ransomware attack. Organisations should have regular and complete data backups that are stored offsite. This will ensure that they can restore their data if it is lost or stolen.
- Develop a data breach response plan: A data breach response plan outlines the steps that an organisation will take in the event of an attack. This plan should include procedures for identifying and containing the breach, eradicating the malware, recovering the data, and notifying affected parties.
- Educate employees on cybersecurity best practices: Employees are often the weakest link in the cybersecurity chain. By educating employees on cybersecurity best practices, organisations can help prevent them from making mistakes that could lead to the attack. Training should cover topics such as phishing scams, social engineering, and password hygiene.
- Use secure software: Install reputable antivirus software and firewalls. This software can detect and block ransomware attacks.
- Avoid clicking on suspicious links or attachments: Do not click on any links or open any attachments in emails that you are not expecting or from senders you do not know. It is often spread through phishing emails that contain malicious links or attachments.
- Keep your software up to date: Regularly check for and install software updates. These updates often contain security patches that can help to protect against newly discovered ransomware threats.
- Back up your data regularly: Regularly back up your important data to an external hard drive or cloud storage service. This will ensure that you have a copy of your data in case it is encrypted by ransomware.
By following these tips, you can help to protect your organisation from ransomware attacks.
Communicating and Mitigating Impact
Notifying Stakeholders, Employees, and Customers about the Incident
Prompt and transparent communication is crucial during and after a ransomware attack. Organisations should notify stakeholders, including employees, customers, partners, and the media, as soon as possible after the attack is detected.
The communication should be clear, concise, and honest, and it should provide the following information:
- The nature of the attack
- The affected systems or data
- The steps that the organisation is taking to address the attack
- Any potential impact on operations, services, or customer data
- The plans for restoring affected systems and data
Addressing Reputational and Financial Implications of the Attack
Ransomware attacks can have significant reputational and financial implications for organisations. Businesses may experience a loss of customer trust, damage to their brand reputation, and increased costs due to downtime, data restoration, and legal fees.
To mitigate these risks, organisations should implement a comprehensive crisis communication plan that addresses the following:
- Identifying and addressing potential public relations issues
- Managing media inquiries and press releases
- Maintaining transparency and open communication with stakeholders
- Restoring customer confidence and rebuilding trust
Rebuilding Trust and Credibility with Stakeholders
Regaining stakeholder trust after a ransomware attack is essential for business continuity and long-term success. Organisations should take the following steps to rebuild trust:
- Conduct a thorough investigation of the attack and take disciplinary action against any employees involved in the incident.
- Implement improved security measures to prevent future attacks.
- Strengthen customer communication and data privacy practices.
- Provide regular updates on the progress of the recovery effort.
- Demonstrate commitment to ethical business practices and data security.
Best Practices for Ransomware Recovery
Regularly Updating Security Software and Patches
Keeping software up to date is essential for preventing ransomware attacks. This includes updating:
- Operating system: The operating system is the foundation of your computer system and is a prime target for ransomware attacks. Regularly updating the operating system will ensure that you have the latest security patches installed.
- Applications: Many applications, such as web browsers, email clients, and antivirus software, have security patches that can be installed to protect against known vulnerabilities.
- Firmware: Firmware is the software that controls the hardware of your computer system. In some cases, firmware updates can be used to patch vulnerabilities that are not accessible from the operating system.
Educating Employees on Recognising and Preventing Ransomware Attacks
Employees are often the weakest link in the cybersecurity chain. They can accidentally click on malicious links, open infected attachments, or provide sensitive information to phishing scammers. To prevent ransomware attacks, it is important to educate employees on the following:
- What ransomware is: Ransomware is a type of malware that encrypts files and holds them hostage until a ransom is paid.
- How ransomware spreads: Ransomware typically spreads through phishing emails, malicious websites, or USB drives.
- How to recognise ransomware: Employees should be able to identify signs of a ransomware attack, such as unusual pop-ups, error messages, or changes to file permissions.
- How to prevent ransomware: Employees should be trained on safe online habits, such as not clicking on suspicious links or opening attachments from unknown senders.
The Role of Cybersecurity in Ransomware Recovery

The Significance of a Cybersecurity Incident Response Plan
A cybersecurity incident response plan is a critical tool for organisations to have in place. This plan should outline the steps that an organisation will take in the event of a cybersecurity incident, such as a ransomware attack. A well-written incident response plan can help organisations minimise the impact of a cybersecurity incident and recover more quickly.
Here are some of the key elements of a cybersecurity incident response plan:
- Identification and containment: The plan should outline the steps that will be taken to identify and contain a cybersecurity incident. This includes steps such as isolating the affected systems, stopping the spread of the infection, and notifying affected parties.
- Eradication: The plan should outline the steps that will be taken to eradicate the malware or other threat that caused the cybersecurity incident. This may involve removing the malware from infected systems, restoring damaged data, and updating software to patch vulnerabilities.
- Recovery: The plan should outline the steps that will be taken to recover from the cybersecurity incident. This may involve restoring systems from backups, reconfiguring networks, and retraining employees on cybersecurity best practices.
- Communication: The plan should outline the steps that will be taken to communicate with affected parties. This may involve notifying customers, partners, and the media.
- Post-incident review: The plan should outline the steps that will be taken to review the incident and learn from it. This can help to prevent future incidents from occurring.
Leveraging Cybersecurity Experts and Resources for Recovery
In the event of a ransomware attack, it is important to have access to cybersecurity experts and resources. These experts can help to assess the situation, develop a recovery plan, and implement the plan. There are many resources available to help organisations recover from ransomware attacks. These resources include:
- The National Cybersecurity and Communications Integration Center (NCCIC): The NCCIC is a 24/7 operations centre that provides cybersecurity threat intelligence and response support to federal, state, local, tribal, and territorial governments and the private sector.
- The Cybersecurity and Infrastructure Security Agency (CISA): CISA is a federal agency that provides cybersecurity and infrastructure security support to critical infrastructure.
- The private sector: Many private sector companies offer cybersecurity incident response services. These companies can provide expert advice and assistance to organisations that have been affected by ransomware attacks.
By following these tips and leveraging the resources available, organisations can increase their chances of recovering from ransomware attacks and minimising the damage.
In conclusion, Ransomware is a serious cyber threat that can have devastating consequences for businesses and individuals. By following best practices for prevention and recovery, organisations can significantly reduce their risk of being targeted by ransomware attacks.
