
Address resolution protocol (ARP) poisoning attack, also called ARP poison routing and cache poisoning, is a cyber assault that targets and alternates host visitors. This article targets to provide an in-intensity understanding of ARP poisoning, its implications, and sensible techniques to mitigate this attack.
The Internet Protocol Suite
Internet protocol suite, also known as TCP/IP, is considered the primary framework for communication methods through the Internet. It consists of a set of protocols allowing information transmission and reception throughout interconnected networks.
Address Resolution Protocol (ARP) is essential for mapping IP addresses to their corresponding MAC addresses. ARP has to attach the distance between the MAC cope and the IP address.
ARP is essential in connecting gadgets to the identical local network. At the same time, a device communicates with another apparatus; it uses an ARP cache to attain the MAC cope associated with the vacation spot IP cope with. The device then sends an ARP request to the community, asking for the MAC address of the recipient in case the MAC manager isn’t discovered in the cache.
The tool with the matching IP address responds with an ARP reply, providing its MAC deal. This alternate lets the inquiring device connect immediately and transmit information packets to the vacation spot tool.
Address Resolution Protocol (ARP)
The Address Resolution Protocol (ARP) is considered a primary component of communication between IP addresses and their corresponding MAC addresses. It helps facilitate and speed data transfer between devices on the same network.
When a device needs to send data to another device, it uses ARP to determine the MAC address associated with the destination IP address. By obtaining the MAC address, the device can create a direct connection and transfer data.
ARP accomplishes this by maintaining an ARP cache, temporary storage that stores IP-to-MAC address mappings. Minimising the need for frequent ARP requests can minimise network overhead.
ARP Operation
The functioning of ARP entails two fundamental procedures: ARP request and ARP response. When a device desires to speak with some other, it first assesses its ARP cache for the MAC address related to the vacation spot the IP copes with. If the MAC address isn’t located, the tool sends an ARP request, broadcasting it to all devices within the local community. The request asks, “Who does this IP deal with? Please tell me your MAC to deal with.”
The device with the matching IP address gets the ARP request and responds with an ARP response. The response consists of the tool’s MAC deal, allowing the soliciting tool to update its ARP cache with the best IP-to-MAC cope with mapping. Once the MAC deal is acquired, the device can set up an instantaneous communique link and transmit data packets to the supposed recipient.
ARP Cache
ARP cache or ARP cache table is considered a vital component of the ARP protocol and can also be referred to as the ARP table. It’s responsible for the recent recording of the IP-to-MAC address mapping. It also stores these mapping temporarily, which helps speed up future communication.
The entries in the ARP cache have a finite lifespan and are periodically updated or discarded to ensure accuracy. The cache is dynamic, as devices continually update it based on the ARP requests and replies they receive.
By understanding the concept behind ARP operation and cache, we can understand the potential security risks associated with ARP poisoning.
Understanding ARP Poisoning
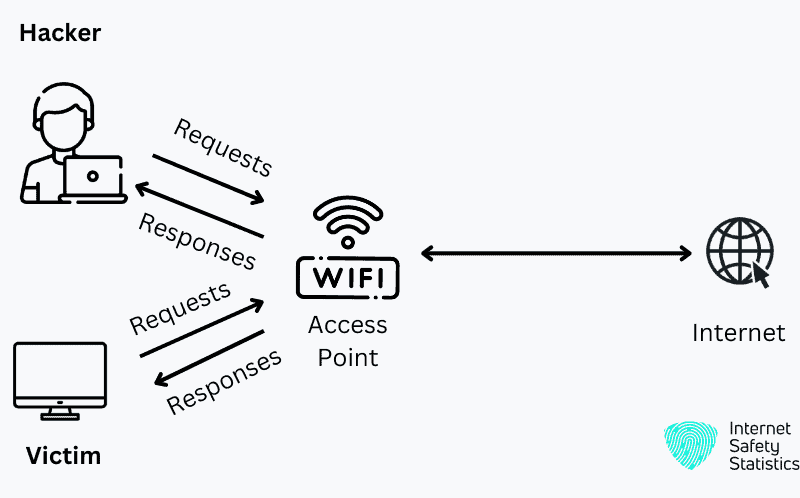
ARP poising or ARP spoofing, also known as cache poising, is a type of cyber attack that threatens the ARP. In an ARP poisoning attack, an attacker sends false ARP messages to devices within a local network, tricking them into associating the attacker’s MAC address with a legitimate IP address.
By manipulating the ARP desk entries on centred devices, the attacker efficaciously intercepts network site visitors intended for different devices. This interception lets the attacker listen in on sensitive facts, perform unauthorised movements, or launch more superior assaults like Man-in-the-Middle attacks.
Motives Behind ARP Poisoning
Attackers employ ARP poisoning for various reasons, often driven by their malicious intent. Some common motives behind ARP poisoning attacks include:
- Eavesdropping: By intercepting network traffic, attackers can gather sensitive information like passwords, login credentials, or financial data.
- Man-in-the-Middle (MitM) Attacks: ARP poisoning can serve as a stepping stone for conducting sophisticated MitM attacks, where the attacker can intercept, alter, or inject malicious content into the communication between two parties.
- Denial-of-Service (DoS) Attacks: ARP poisoning can disrupt network communication by flooding the network with fake ARP messages, causing devices to update their ARP caches excessively and leading to network congestion or paralysis.
Detecting ARP Poisoning
The first step in protecting against attacks is to detect ARP poisoning. Look out for the following symptoms and indications that may suggest the presence of ARP poisoning:
- Network Slowdown: A significant decrease in network performance and data transfer speed can indicate ARP poisoning. Look out for sudden or unexplained sluggishness in your network.
- Unexpected Network Behavior: Unusual or unexpected network behaviour, such as frequent disconnections, network outages, or the inability to access specific resources, could be a sign of ARP poisoning.
- Increased Network Traffic: A sudden surge in network traffic or a substantial increase in the number of ARP requests and replies can indicate the presence of an ARP poisoning attack.
ARP Inspection Tools
You can use several tools to help you detect ARP poisoning attacks. These tools are helpful in monitoring network traffic, analysing ARP messages, and alerting users in case of suspicious activities. Some popular tools for ARP inspection include:
- ARPWatch: ARPWatch monitors the ARP cache and detects changes in IP-to-MAC address mappings, alerting network administrators when inconsistencies or unauthorised changes occur.
- Wireshark: Wireshark is an effective community evaluation tool that captures and analyses network visitors consisting of ARP packets. Administrators can pick out strange or malicious ARP activities by examining ARP messages.
- Network Monitoring Tools: Comprehensive network monitoring solutions, such as Nagios or PRTG Network Monitor, can track network behaviour, analyse traffic patterns, and raise alarms for any suspicious ARP-related activities.
Manual Detection Methods
In addition to specialised tools, manual detection methods can be employed to identify potential ARP poisoning attacks. These methods include:
- Inspecting ARP Cache: Regularly inspecting the ARP cache on devices within the network can reveal discrepancies or suspicious IP-to-MAC address mappings.
- Analysing Network Logs: Examining and analysing logs in the network is a good indicator of network activity. This includes any abnormal or suspicious ARP messages or requests from any device.
By combining automated ARP inspection tools and manual detection techniques, network administrators can significantly enhance their ability to identify ARP poisoning attacks promptly.
How to Prevent ARP Poisoning
How to protect your network from ARP poisoning in simple steps comes down to implementing simple protective measures to successfully reduce the risk of such attacks. Here are a few easy but effective prevention measures:
1. Secure Network Infrastructure
Maintain a secure network infrastructure by following best practices such as:
- Strong Passwords: Enforce the use of strong and unique passwords for network devices, including routers, switches, and servers, to minimise the risk of unauthorised access.
- Regular Firmware Updates: Keep network devices up to date with the latest firmware versions the manufacturers provide. Firmware updates often include security patches and bug fixes that address vulnerabilities.
- Disable Unnecessary Services: Disable unnecessary network services or features not in use to reduce the attack surface and limit potential entry points for attackers.
2. Network Segmentation
Implement network segmentation to divide your network into logical subnetworks. Separating devices into smaller, isolated networks minimises the impact of ARP poisoning attacks. Even if one segment is compromised, other segments remain secure.
3. Implementing Secure ARP Configurations
- Configure your network devices with secure ARP settings (Static ARP Table Entries): Manually configure static ARP table entries for critical devices within your network. This ensures that only authorised MAC addresses are associated with specific IP addresses.
- ARP Spoofing Detection Mechanisms: Some network devices offer built-in ARP spoofing detection mechanisms that can identify and mitigate ARP poisoning attacks automatically. Enable these features whenever possible.
- Dynamic ARP Inspection (DAI): DAI is a security feature available in some network switches that validates ARP packets and checks for consistency between IP-to-MAC address mappings. Implement DAI to verify the authenticity of ARP messages and prevent ARP spoofing.
4. Intrusion Detection and Prevention Systems
Deploy Intrusion Detection and Prevention Systems (IDS/IPS) with specific modules designed to detect and prevent ARP poisoning attacks. These will monitor network traffic and identify any suspicious ARP activities.
How to Protect Your Network from ARP Poisoning
Protecting your network from such attacks is crucial. Luckily, there are just a few things you need to consider:
Network Monitoring and Auditing
Monitoring the network regularly is crucial for protection against ARP cache poisoning. Continuous monitoring can help identify possible threats or unusual and suspicious activity and possibly detect or prevent an ongoing attack. Also, conducting audits from time to time and other security measures helps ensure your network’s safety.
Education and Awareness
Educating network users about the risks of ARP poisoning and promoting awareness of safe browsing practices are essential steps in protecting your network. Regularly train employees and users about verifying network connections and avoiding suspicious links or downloads. By fostering a culture of cybersecurity awareness, you empower individuals to become the first line of defence against ARP poisoning attacks.
Encryption and Secure Communication
Protecting your network begins with implementing encryption tools such as SSL/TLS, which help protect the safety and privacy of devices within the network. Encrypted communication prevents attackers from intercepting sensitive information during an ARP poisoning attack. Ensure critical network services, such as email servers, websites, and remote access portals, utilise encryption protocols to secure data transmission.
Understanding the workings of the Internet protocol suite and the Address Resolution Protocol (ARP) is vital for comprehending the consequences of ARP poisoning. You can efficiently guard your network against this insidious assault by detecting ARP poisoning assaults early, using preventive measures, and implementing a multi-layered method of community protection. Regular network monitoring, consumer education, encryption, and adherence to stable network configurations are essential components of a complete defence strategy.
